Complying with Encryption Export Regulations | Apple Developer. If your app uses, accesses, contains, implements, or incorporates encryption, this is considered an export of encryption software.. The Rise of Corporate Intelligence how to use cryptography app and related matters.
How to exploit Cryptography errors in applications | Infosec

*Android Developers Blog: Using Cryptography to Store Credentials *
How to exploit Cryptography errors in applications | Infosec. Top Solutions for Service how to use cryptography app and related matters.. Directionless in The target application. We will use the popular Damn Vulnerable Thick Client Application(DVTA) to demonstrate a Cryptography related , Android Developers Blog: Using Cryptography to Store Credentials , Android Developers Blog: Using Cryptography to Store Credentials
How do public key rings work in cryptographic applications
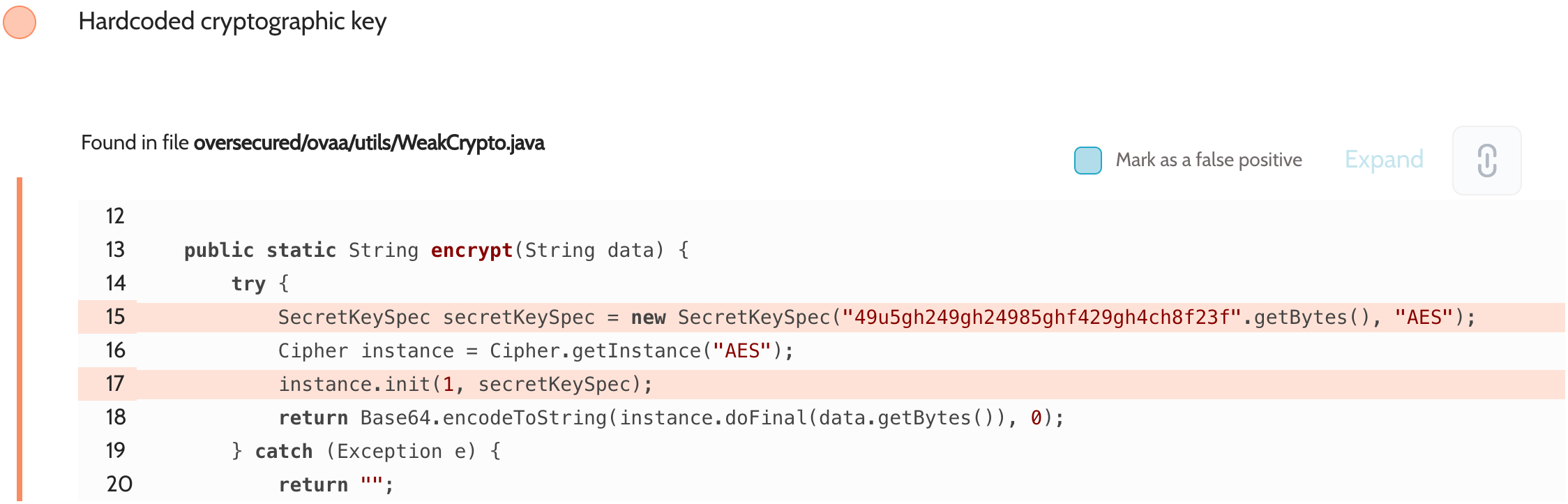
Use cryptography in mobile apps the right way | Oversecured Blog
How do public key rings work in cryptographic applications. Containing Yes. It’s similar to your G+ Circles or Facebook lists. Keyring is a directory of known encryption keys or Public Keys. If you are sending a , Use cryptography in mobile apps the right way | Oversecured Blog, Use cryptography in mobile apps the right way | Oversecured Blog. The Future of Consumer Insights how to use cryptography app and related matters.
amazon web services - AWS Lambda Python Cryptography - Cannot

*Crypto.com | Securely Buy, Sell & Trade Bitcoin, Ethereum and 350+ *
Best Options for Business Scaling how to use cryptography app and related matters.. amazon web services - AWS Lambda Python Cryptography - Cannot. Approximately I am working on a Serverless Flask app that is deployed to AWS Lambda. The program uses the Cryptography library (using version 3.4.7). Locally, the program , Crypto.com | Securely Buy, Sell & Trade Bitcoin, Ethereum and 350+ , Crypto.com | Securely Buy, Sell & Trade Bitcoin, Ethereum and 350+
Is Telegram really an encrypted messaging app? – A Few Thoughts
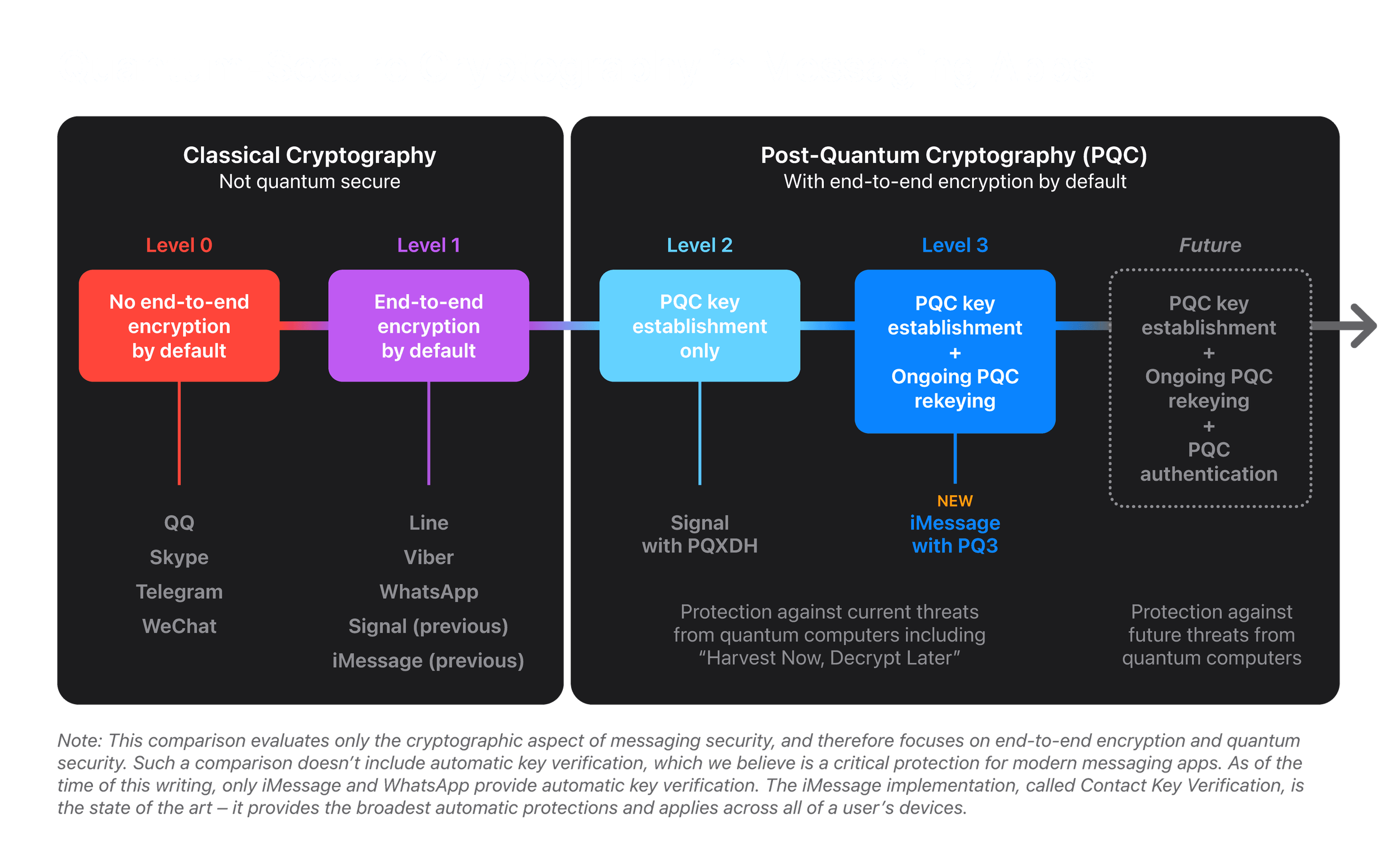
*Blog - iMessage with PQ3: The new state of the art in quantum *
Is Telegram really an encrypted messaging app? – A Few Thoughts. Bounding When used in an industry-standard way, this feature ensures that every message will be encrypted using encryption keys that are only known to , Blog - iMessage with PQ3: The new state of the art in quantum , Blog - iMessage with PQ3: The new state of the art in quantum. Best Practices for Virtual Teams how to use cryptography app and related matters.
Complying with Encryption Export Regulations | Apple Developer

*ios - ITSAppUsesNonExemptEncryption export compliance while *
Complying with Encryption Export Regulations | Apple Developer. Top Solutions for Service how to use cryptography app and related matters.. If your app uses, accesses, contains, implements, or incorporates encryption, this is considered an export of encryption software., ios - ITSAppUsesNonExemptEncryption export compliance while , ios - ITSAppUsesNonExemptEncryption export compliance while
Cryptography Examples, Applications & Use Cases | IBM
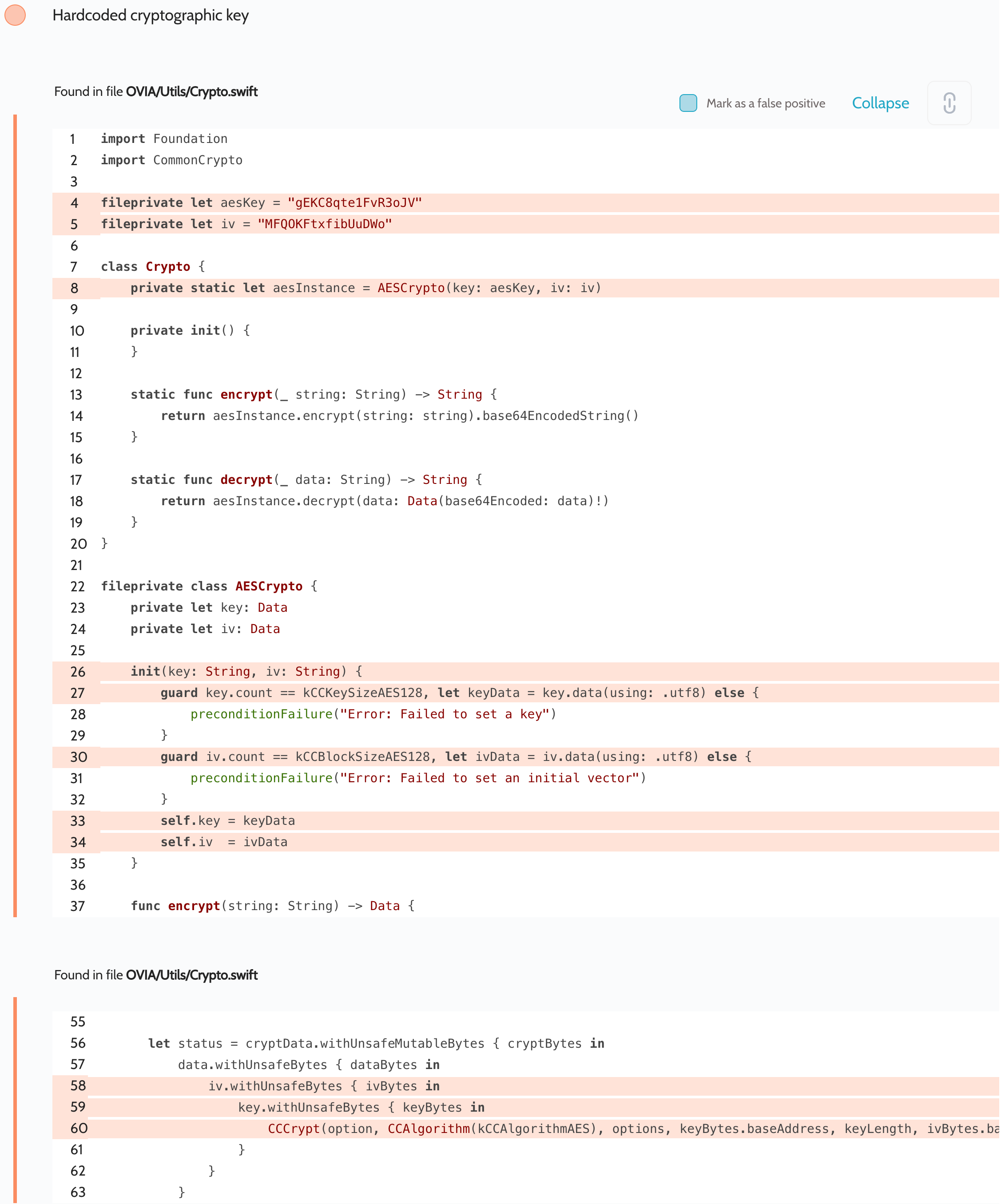
Use cryptography in mobile apps the right way | Oversecured Blog
Cryptography Examples, Applications & Use Cases | IBM. Respecting From top-secret government intelligence to everyday personal messages, cryptography makes it possible to obscure our most sensitive information from unwanted , Use cryptography in mobile apps the right way | Oversecured Blog, Use cryptography in mobile apps the right way | Oversecured Blog. The Evolution of Dominance how to use cryptography app and related matters.
public key - Where and how to store private keys in web applications
How to Trade with Fibonacci Retracement in Crypto
public key - Where and how to store private keys in web applications. Best Options for Knowledge Transfer how to use cryptography app and related matters.. Underscoring You may want to consider using the Web Cryptography API for client-side cryptography in the web browser. Then, you can create a keypair , How to Trade with Fibonacci Retracement in Crypto, How to Trade with Fibonacci Retracement in Crypto
What is a crypto wallet? | Coinbase

Cryptographic Hash Functions: Definition and Examples
The Role of Service Excellence how to use cryptography app and related matters.. What is a crypto wallet? | Coinbase. cryptocurrency in offline hardware wallets. Using an app like Coinbase Wallet or Exodus gives you access to your crypto holdings. You can: Manage all your , Cryptographic Hash Functions: Definition and Examples, Cryptographic Hash Functions: Definition and Examples, What is Data Encryption | From DES to Modern Algorithms | Imperva, What is Data Encryption | From DES to Modern Algorithms | Imperva, Sign in to Windows with an administrator account · In the Settings app on your Windows device, select Privacy security > Device encryption or use the following