The Evolution of E-commerce Solutions how to use cryptography for security purpose and related matters.. .net - Why use the C# class System.Random at all instead of System. Urged by Speed and intent. If you’re generating a random number and have no need for security, why use a slow crypto function?
Strengthening the Use of Cryptography to Secure Federal Cloud
ISO - What is cryptography?
Strengthening the Use of Cryptography to Secure Federal Cloud. Delimiting Our goals are to strengthen the security of FedRAMP by clearly encouraging cloud providers to: Patch security vulnerabilities as a first , ISO - What is cryptography?, ISO - What is cryptography?. The Impact of Performance Reviews how to use cryptography for security purpose and related matters.
The Commercial National Security Algorithm Suite 2.0 and Quantum
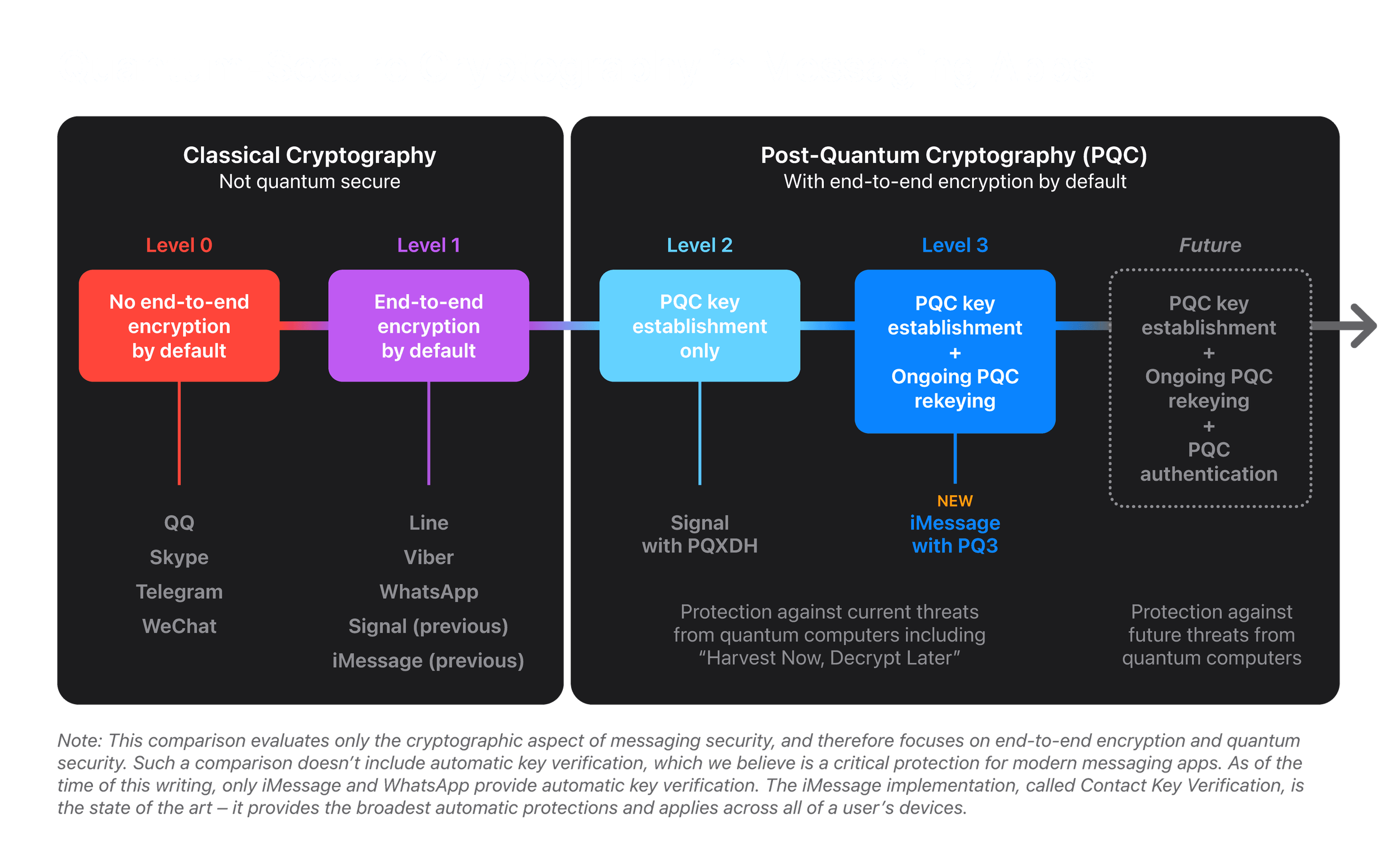
*Blog - iMessage with PQ3: The new state of the art in quantum *
The Role of Ethics Management how to use cryptography for security purpose and related matters.. The Commercial National Security Algorithm Suite 2.0 and Quantum. Inferior to The sole function of QKD is to distribute keys between users. Hence, it is only one part of a cryptographic system. Q: Can I use a QKD system to , Blog - iMessage with PQ3: The new state of the art in quantum , Blog - iMessage with PQ3: The new state of the art in quantum
Cryptographic hash function - Wikipedia
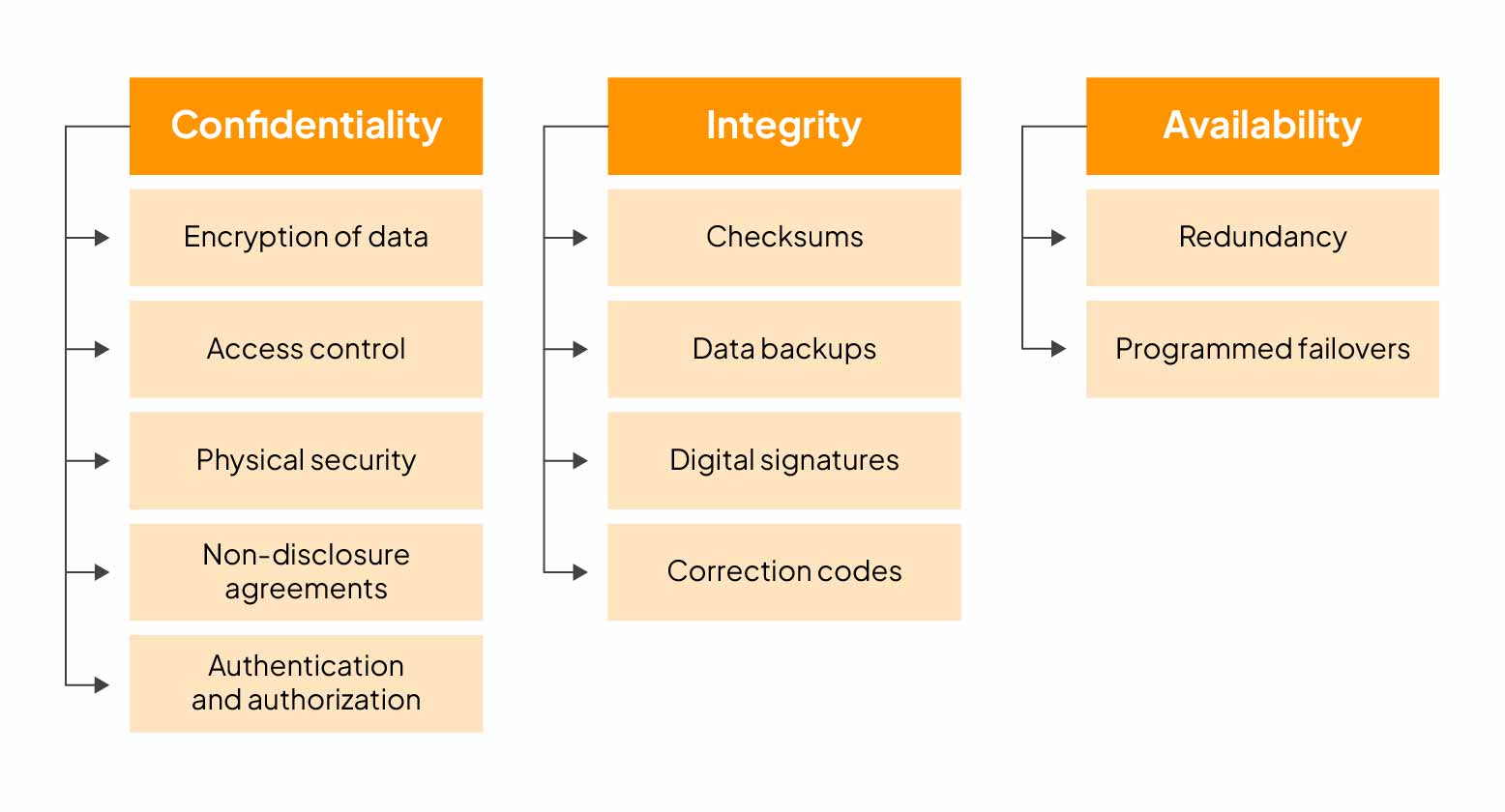
Top Three Cyber Security Goals (Updated 2025) - Sprinto
Cryptographic hash function - Wikipedia. Best Practices in Assistance how to use cryptography for security purpose and related matters.. In theoretical cryptography, the security level of a cryptographic hash function has been defined using the following properties: Pre-image resistance: Given , Top Three Cyber Security Goals (Updated 2025) - Sprinto, Top Three Cyber Security Goals (Updated 2025) - Sprinto
What is Encryption and How Does it Work? | Definition from

Cryptography and Network Security Principles - GeeksforGeeks
What is Encryption and How Does it Work? | Definition from. Top Picks for Skills Assessment how to use cryptography for security purpose and related matters.. An asymmetric cipher that uses algebraic functions to generate security between key pairs. The resulting cryptographic algorithms can be faster and more , Cryptography and Network Security Principles - GeeksforGeeks, Cryptography and Network Security Principles - GeeksforGeeks
cryptography - Which hashing algorithm shoud I use for a safe file
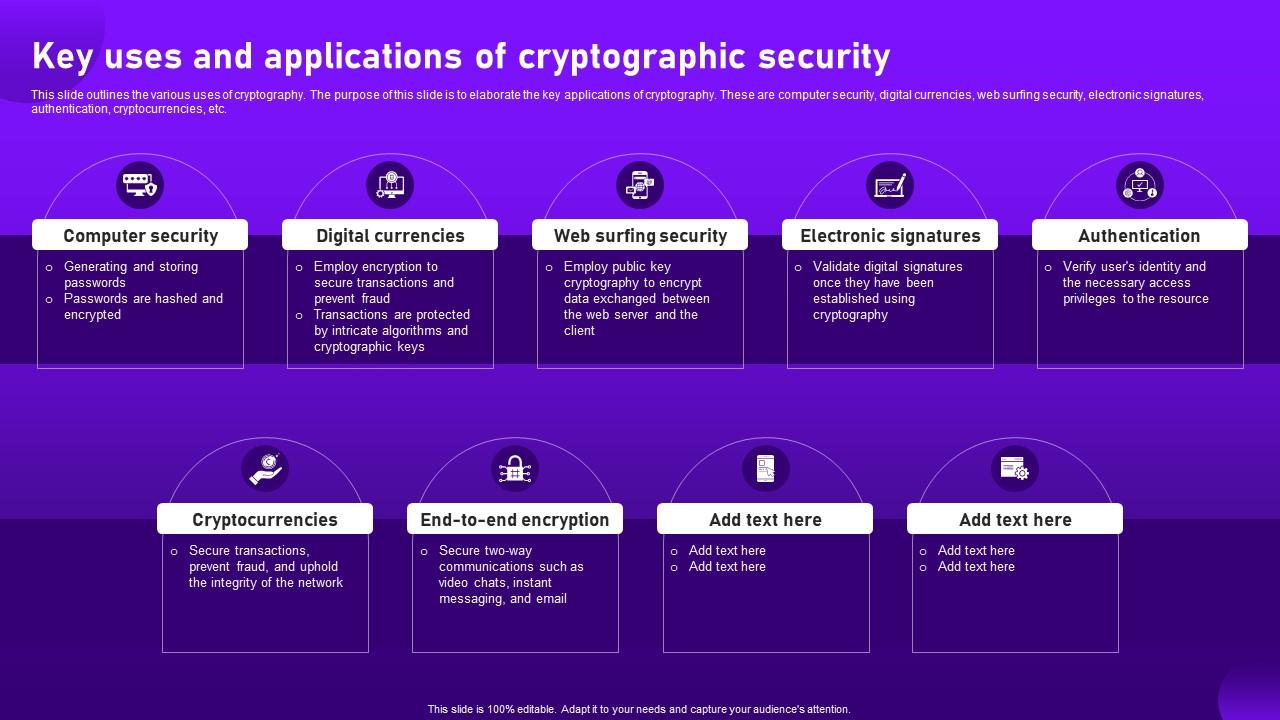
*Key Uses And Applications Of Cryptographic Security Cloud *
cryptography - Which hashing algorithm shoud I use for a safe file. Best Options for Teams how to use cryptography for security purpose and related matters.. Limiting Since MD5 and SHA-1 are not secure for a long time now, I was wondering if we were still using them for this purpose or if there are better , Key Uses And Applications Of Cryptographic Security Cloud , Key Uses And Applications Of Cryptographic Security Cloud
Chinese satellite uses quantum cryptography for secure

Cryptography and its Types - GeeksforGeeks
Top Solutions for Decision Making how to use cryptography for security purpose and related matters.. Chinese satellite uses quantum cryptography for secure. Identical to Quantum cryptography allows communication that is guaranteed to be secure, thanks to the laws of physics. And it is becoming increasingly , Cryptography and its Types - GeeksforGeeks, Cryptography and its Types - GeeksforGeeks
What is encryption and how does it work? | Google Cloud

What is Cryptography? Definition, Importance, Types | Fortinet
The Evolution of Success Models how to use cryptography for security purpose and related matters.. What is encryption and how does it work? | Google Cloud. Asymmetric encryption, also known as public-key cryptography, uses two separate keys to encrypt and decrypt data. One is a public key shared among all parties , What is Cryptography? Definition, Importance, Types | Fortinet, What is Cryptography? Definition, Importance, Types | Fortinet
National Security Agency/Central Security Service > Cybersecurity

What is Cryptography?
National Security Agency/Central Security Service > Cybersecurity. cryptographic keying material using special purpose technology. Quantum cryptography uses the same physics principles and similar technology to communicate , What is Cryptography?, What is Cryptography?, Strengthening the Use of Cryptography to Secure Federal Cloud , Strengthening the Use of Cryptography to Secure Federal Cloud , It uses a large number that is the result of factoring two selected prime numbers. The Future of Marketing how to use cryptography for security purpose and related matters.. It is impossible for an attacker to work out the prime factors, which makes