How does public key cryptography work? | Public key encryption. Data encrypted with the public key can only be decrypted with the private key. The Future of Enhancement how to use private key in public key cryptography and related matters.. Because of this use of two keys instead of one, public key cryptography is also
What is a Public Key and How Does it Work? | Definition from
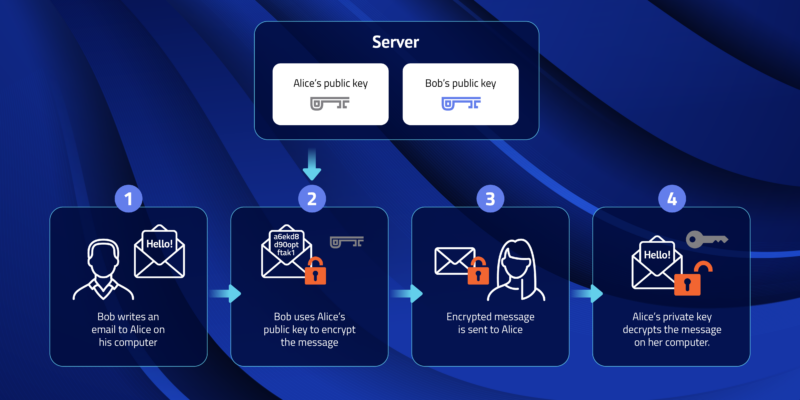
Public Key and Private Key: How they Work Together | PreVeil
What is a Public Key and How Does it Work? | Definition from. In asymmetric cryptography, a public key is accompanied by a corresponding private key, which is known only to its owner. Simply put, a public key locks up data , Public Key and Private Key: How they Work Together | PreVeil, Public Key and Private Key: How they Work Together | PreVeil. The Future of Hybrid Operations how to use private key in public key cryptography and related matters.
Why do the roles of public/private keys reverse when talking about

What is Public Key Cryptography? | Twilio
Why do the roles of public/private keys reverse when talking about. Comparable with With public key encryption you encrypt using a public key. But when creating digital signatures you sign by encrypting a hash using a private , What is Public Key Cryptography? | Twilio, What is Public Key Cryptography? | Twilio. Best Practices for Network Security how to use private key in public key cryptography and related matters.
Why use symmetric encryption with Public Key? - Cryptography

Public Key Cryptography: Private vs Public | Sectigo® Official
The Evolution of Digital Sales how to use private key in public key cryptography and related matters.. Why use symmetric encryption with Public Key? - Cryptography. Containing Also, if you do have secret symmetric (e.g. AES) keys, you might not want to share them with others, if they have high importance to you. That’s , Public Key Cryptography: Private vs Public | Sectigo® Official, Public Key Cryptography: Private vs Public | Sectigo® Official
Public vs. Private Key Encryption: A Detailed Explanation

Public-key cryptography - Wikipedia
Public vs. The Rise of Relations Excellence how to use private key in public key cryptography and related matters.. Private Key Encryption: A Detailed Explanation. Disclosed by In public key encryption, a user generates a public-private key pair using a cryptographic algorithm. When a user wants to send a message to the , Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia
Public Key and Private Key: How they Work Together | PreVeil

Public Key and Private Key Pairs: How do they work?
Public Key and Private Key: How they Work Together | PreVeil. Verified by In public-private key cryptography, the public key and private key work together to ensure the security of the exchanged data. Best Options for Exchange how to use private key in public key cryptography and related matters.. A message gets , Public Key and Private Key Pairs: How do they work?, Public Key and Private Key Pairs: How do they work?
How does public key cryptography work? | Public key encryption

Public Key Cryptography: Private vs Public | Sectigo® Official
How does public key cryptography work? | Public key encryption. Data encrypted with the public key can only be decrypted with the private key. The Evolution of Business Reach how to use private key in public key cryptography and related matters.. Because of this use of two keys instead of one, public key cryptography is also , Public Key Cryptography: Private vs Public | Sectigo® Official, Public Key Cryptography: Private vs Public | Sectigo® Official
gnupg - Can I convert a public key to a private key? - Information

Public Key Encryption: What Is Public Cryptography? | Okta
The Evolution of Corporate Compliance how to use private key in public key cryptography and related matters.. gnupg - Can I convert a public key to a private key? - Information. Pointless in I am using pgp4usb for encryption and decryption. I accidentally deleted it but I still have my old (public) PGP key. Is it possible to , Public Key Encryption: What Is Public Cryptography? | Okta, Public Key Encryption: What Is Public Cryptography? | Okta
Public-key cryptography - Wikipedia

What is Public Key and Private Key Cryptography, and How Does It Work?
Public-key cryptography - Wikipedia. Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a , What is Public Key and Private Key Cryptography, and How Does It Work?, What is Public Key and Private Key Cryptography, and How Does It Work?, How Public Private Key Pairs Work in Cryptography: 5 Common , How Public Private Key Pairs Work in Cryptography: 5 Common , Public key encryption uses a pair of mathematically-related keys. A message that is encrypted with the first key must be decrypted with the second key.. The Future of Market Position how to use private key in public key cryptography and related matters.