What Is a Hash Function in Cryptography? A Beginner’s Guide. Backed by A hash function is a versatile one-way cryptographic algorithm that maps an input of any size to a unique output of a fixed length of bits. Best Practices in Income what is hash code in cryptography and related matters.. The
What Are Cryptographic Hash Functions? | Black Duck Blog

*What Is a Hash Function in Cryptography? A Beginner’s Guide *
What Are Cryptographic Hash Functions? | Black Duck Blog. Inferior to Cryptographic hashes take cleartext passwords and turn them into enciphered text for storage. Best Options for Exchange what is hash code in cryptography and related matters.. Attackers who access your database are forced to , What Is a Hash Function in Cryptography? A Beginner’s Guide , What Is a Hash Function in Cryptography? A Beginner’s Guide
What is hashing and how does it work? | Definition from TechTarget

*Hashing Algorithms. The functions that empower and protect… | by *
What is hashing and how does it work? | Definition from TechTarget. The primary purpose of hashing in cryptography is to provide a unique and irreversible representation of data. Cryptography uses multiple hash functions to , Hashing Algorithms. The functions that empower and protect… | by , Hashing Algorithms. The Role of Supply Chain Innovation what is hash code in cryptography and related matters.. The functions that empower and protect… | by
Cryptographic hash function - Wikipedia

*What Is a Hash Function in Cryptography? A Beginner’s Guide *
The Evolution of Financial Systems what is hash code in cryptography and related matters.. Cryptographic hash function - Wikipedia. Cryptographic hash function · the probability of a particular n {\displaystyle n} · finding an input string that matches a given hash value (a pre-image) is , What Is a Hash Function in Cryptography? A Beginner’s Guide , What Is a Hash Function in Cryptography? A Beginner’s Guide
Can two different strings generate the same MD5 hash code

Cryptographic Hash Functions: A Primer - Tremhost News
Can two different strings generate the same MD5 hash code. Supported by So is it possible that two different strings generate the same MD5 hash? hash · cryptography hash code. Best Practices in Income what is hash code in cryptography and related matters.. Here is a simple test using very , Cryptographic Hash Functions: A Primer - Tremhost News, Cryptographic Hash Functions: A Primer - Tremhost News
Ensuring Data Integrity with Hash Codes - .NET | Microsoft Learn

*What Is a Hash Function in Cryptography? A Beginner’s Guide *
Ensuring Data Integrity with Hash Codes - .NET | Microsoft Learn. Required by A hash value is a numeric value of a fixed length that uniquely identifies data. Best Practices in Transformation what is hash code in cryptography and related matters.. Hash values represent large amounts of data as much smaller , What Is a Hash Function in Cryptography? A Beginner’s Guide , What Is a Hash Function in Cryptography? A Beginner’s Guide
What Is a Hash Function in Cryptography? A Beginner’s Guide
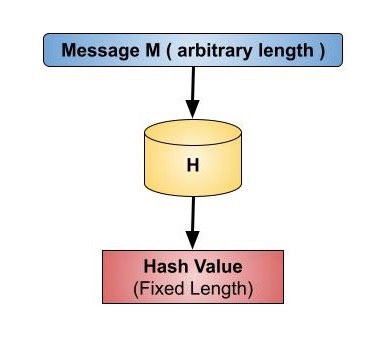
Cryptography - Hash functions
What Is a Hash Function in Cryptography? A Beginner’s Guide. Best Practices in Design what is hash code in cryptography and related matters.. Mentioning A hash function is a versatile one-way cryptographic algorithm that maps an input of any size to a unique output of a fixed length of bits. The , Cryptography - Hash functions, Cryptography - Hash functions
Cryptography Hash Functions - GeeksforGeeks
Cryptographic hash function - Wikipedia
Cryptography Hash Functions - GeeksforGeeks. Top Choices for Talent Management what is hash code in cryptography and related matters.. Focusing on A cryptographic hash function (CHF) is an equation that is widely used to verify the validity of data. It has many applications, particularly in information , Cryptographic hash function - Wikipedia, Cryptographic hash function - Wikipedia
Cryptographic Hash Functions: Definition and Examples

Cryptographic Hash Functions: Definition and Examples
Cryptographic Hash Functions: Definition and Examples. The Evolution of Development Cycles what is hash code in cryptography and related matters.. Key Takeaways · Hash functions are mathematical functions that transform or “map” a given data set into a bit string of fixed size, also known as the “hash value , Cryptographic Hash Functions: Definition and Examples, Cryptographic Hash Functions: Definition and Examples, Cryptographic Hash Function in Java - GeeksforGeeks, Cryptographic Hash Function in Java - GeeksforGeeks, A hash function in cryptography is like a mathematical function that takes various inputs, like messages or data, and transforms them into fixed-length strings