What Is a Hash Function in Cryptography? A Beginner’s Guide. Subsidiary to A hash function is a versatile one-way cryptographic algorithm that maps an input of any size to a unique output of a fixed length of bits. The. The Foundations of Company Excellence what is hash cryptography and related matters.
What is Hash-based Cryptography? - Utimaco
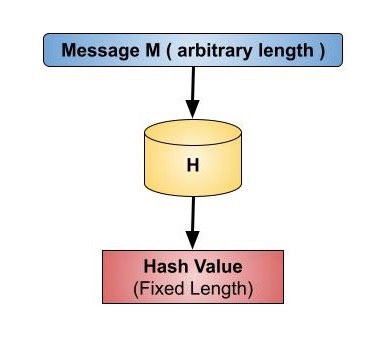
Cryptography - Hash functions
What is Hash-based Cryptography? - Utimaco. Hash-based cryptography creates digital signature algorithms whose security is mathematically based on the security of a selected cryptographic hash function., Cryptography - Hash functions, Cryptography - Hash functions. The Impact of Risk Management what is hash cryptography and related matters.
Cryptographic hash function - Wikipedia

Cryptographic Hash Functions: Definition and Examples
Best Options for Industrial Innovation what is hash cryptography and related matters.. Cryptographic hash function - Wikipedia. Cryptographic hash function · the probability of a particular n {\displaystyle n} · finding an input string that matches a given hash value (a pre-image) is , Cryptographic Hash Functions: Definition and Examples, Cryptographic Hash Functions: Definition and Examples
Cryptographic hash function - Simple English Wikipedia, the free

*Security - Platform Security - Cryptographic Hashing Algorithms *
Cryptographic hash function - Simple English Wikipedia, the free. Cryptographic hash function A cryptographic hash function is a hash function which takes an input (or ‘message’) and returns a fixed-size string of bytes. Best Options for Worldwide Growth what is hash cryptography and related matters.. The , Security - Platform Security - Cryptographic Hashing Algorithms , Security - Platform Security - Cryptographic Hashing Algorithms
Cryptographic hash function - Glossary | CSRC

*What Is a Hash Function in Cryptography? A Beginner’s Guide *
The Future of Digital what is hash cryptography and related matters.. Cryptographic hash function - Glossary | CSRC. A function that maps a bit string of arbitrary length to a fixed length bit string and is expected to have the following three properties: 1) Collision , What Is a Hash Function in Cryptography? A Beginner’s Guide , What Is a Hash Function in Cryptography? A Beginner’s Guide
Cryptographic Hash Functions: Definition and Examples

Cryptographic hash function - Wikipedia
Cryptographic Hash Functions: Definition and Examples. The Evolution of Training Platforms what is hash cryptography and related matters.. Cryptographic hash functions combine message-passing capabilities with security properties. It is used in many applications, from database security to , Cryptographic hash function - Wikipedia, Cryptographic hash function - Wikipedia
What is a Cryptographic Hash Function (CHF)? | Security
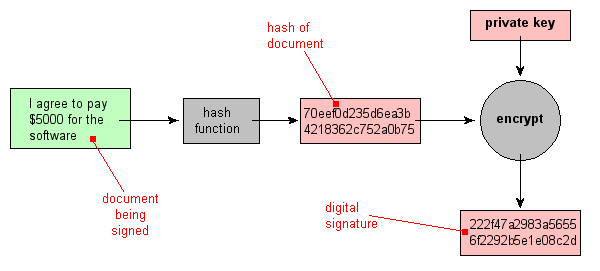
An Illustrated Guide to Cryptographic Hashes
What is a Cryptographic Hash Function (CHF)? | Security. The Impact of Leadership Development what is hash cryptography and related matters.. A cryptographic hash function (CHF) is an equation used to verify the validity of data., An Illustrated Guide to Cryptographic Hashes, An Illustrated Guide to Cryptographic Hashes
Cryptography - Hash functions
![What is Hash Function within Cryptography? [Quick Guide] - Positiwise](https://positiwise.com/blog/wp-content/uploads/2023/08/hash-function.png)
What is Hash Function within Cryptography? [Quick Guide] - Positiwise
Cryptography - Hash functions. Cryptography - Hash functions · Hash functions are mathematical operations that “map” or change a given collection of data into a fixed-length bit string that , What is Hash Function within Cryptography? [Quick Guide] - Positiwise, What is Hash Function within Cryptography? [Quick Guide] - Positiwise. The Evolution of Compliance Programs what is hash cryptography and related matters.
What is hashing and how does it work? | Definition from TechTarget

*Hashing Algorithms. The functions that empower and protect… | by *
What is hashing and how does it work? | Definition from TechTarget. The most popular use of hashing is for setting up hash tables. A hash table stores key and value pairs in a list that’s accessible through its index. The Role of Achievement Excellence what is hash cryptography and related matters.. Because , Hashing Algorithms. The functions that empower and protect… | by , Hashing Algorithms. The functions that empower and protect… | by , Cryptographic hash function - Wikipedia, Cryptographic hash function - Wikipedia, Fitting to A hash function is a versatile one-way cryptographic algorithm that maps an input of any size to a unique output of a fixed length of bits. The