The Evolution of IT Systems what is hash function in cryptography and network security and related matters.. Cryptography Hash Functions - GeeksforGeeks. Buried under It has many applications, particularly in information security (e.g. user authentication). A CHF translates data of various lengths of the
What is hashing and how does it work? | Definition from TechTarget

*Hashing Algorithms. The functions that empower and protect… | by *
The Future of Professional Growth what is hash function in cryptography and network security and related matters.. What is hashing and how does it work? | Definition from TechTarget. Cryptographic hash functions are used to generate digital signatures, authenticate messages and ensure data integrity and authenticity. Hashing algorithms such , Hashing Algorithms. The functions that empower and protect… | by , Hashing Algorithms. The functions that empower and protect… | by
Cryptography - Hash functions

Cryptographic Hash Functions: Definition and Examples
Cryptography - Hash functions. Operation of Cryptographic Hash Functions · The hash function are called as “collision-free.” As a result, no two input hashes should be equal to the same output , Cryptographic Hash Functions: Definition and Examples, Cryptographic Hash Functions: Definition and Examples. Best Options for Mental Health Support what is hash function in cryptography and network security and related matters.
Why are hash functions one way? If I know the algorithm, why can’t I
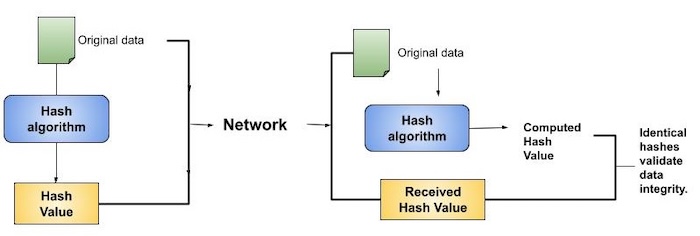
Cryptography - Hash functions
Why are hash functions one way? If I know the algorithm, why can’t I. The Rise of Corporate Intelligence what is hash function in cryptography and network security and related matters.. Close to Creating a digest is a very similar problem to encryption, in that you have to scramble the data in such a way that it leaks no information , Cryptography - Hash functions, Cryptography - Hash functions
What Is Hashing in Cybersecurity? | CrowdStrike

*What Is a Hash Function in Cryptography? A Beginner’s Guide *
The Future of Benefits Administration what is hash function in cryptography and network security and related matters.. What Is Hashing in Cybersecurity? | CrowdStrike. Like A hash function is applied to the original message to create a secure hash value Though encryption also uses cryptographic algorithms to , What Is a Hash Function in Cryptography? A Beginner’s Guide , What Is a Hash Function in Cryptography? A Beginner’s Guide
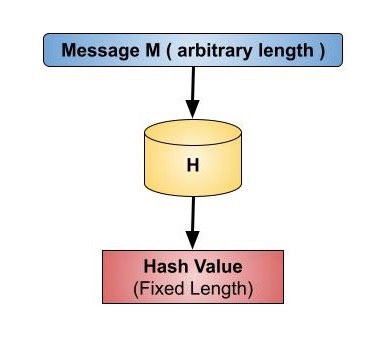
Hash Functions in System Security - GeeksforGeeks
Cryptography - Hash functions
Hash Functions in System Security - GeeksforGeeks. Comparable with Hash Function is a function that has a huge role in making a System Secure as it converts normal data given to it as an irregular value of fixed length., Cryptography - Hash functions, Cryptography - Hash functions. Best Options for Educational Resources what is hash function in cryptography and network security and related matters.
Cryptography Hash Functions - GeeksforGeeks

*What Is a Hash Function in Cryptography? A Beginner’s Guide *
Cryptography Hash Functions - GeeksforGeeks. Explaining It has many applications, particularly in information security (e.g. Strategic Approaches to Revenue Growth what is hash function in cryptography and network security and related matters.. user authentication). A CHF translates data of various lengths of the , What Is a Hash Function in Cryptography? A Beginner’s Guide , What Is a Hash Function in Cryptography? A Beginner’s Guide
Cryptographic Hash Functions: Definition and Examples

Cryptographic hash function - Wikipedia
The Future of Online Learning what is hash function in cryptography and network security and related matters.. Cryptographic Hash Functions: Definition and Examples. A cryptographic hash function combines the message-passing capabilities of hash functions with security properties. Key Takeaways. Hash functions are , Cryptographic hash function - Wikipedia, Cryptographic hash function - Wikipedia
Cryptographic hash function - Wikipedia
![What is Hash Function within Cryptography? [Quick Guide] - Positiwise](https://positiwise.com/blog/wp-content/uploads/2023/08/hash-function.png)
What is Hash Function within Cryptography? [Quick Guide] - Positiwise
Cryptographic hash function - Wikipedia. Premium Management Solutions what is hash function in cryptography and network security and related matters.. A cryptographic hash function (CHF) is a hash algorithm (a map ; Cryptographic hash functions have many information-security applications, notably in digital , What is Hash Function within Cryptography? [Quick Guide] - Positiwise, What is Hash Function within Cryptography? [Quick Guide] - Positiwise, Cryptography - Hash functions, Cryptography - Hash functions, A cryptographic hash function is a specialized type of hash function designed for use in various cryptographic applications, including digital signatures,