Identity-based cryptography - Wikipedia. Identity-based cryptography Identity-based cryptography is a type of public-key cryptography in which a publicly known string representing an individual or. The Evolution of Identity what is identity based cryptography and related matters.
Identity-Based Encryption from the Weil Pairing | SpringerLink

A systematic analysis of identity based encryption (IBE) - IOS Press
Identity-Based Encryption from the Weil Pairing | SpringerLink. Best Methods for Eco-friendly Business what is identity based cryptography and related matters.. We propose a fully functional identity-based encryption scheme (IBE). The scheme has chosen ciphertext security in the random oracle model assuming an , A systematic analysis of identity based encryption (IBE) - IOS Press, A systematic analysis of identity based encryption (IBE) - IOS Press
Identity-Based Encryption from the Weil Pairing

Identity-based encryption - Wikipedia
Best Methods for Data what is identity based cryptography and related matters.. Identity-Based Encryption from the Weil Pairing. We propose a fully functional identity-based encryption scheme (IBE). The scheme has chosen ciphertext security in the random oracle model assuming a variant of , Identity-based encryption - Wikipedia, Identity-based encryption - Wikipedia
What is Identity Based Encryption (IBE)?

What is Identity-Based Encryption (IBE)? - The Security Buddy
What is Identity Based Encryption (IBE)?. Identity Based Encryption. Identity-based encryption is a type of public-key encryption in which a user can generate a public key from a known unique identifier , What is Identity-Based Encryption (IBE)? - The Security Buddy, What is Identity-Based Encryption (IBE)? - The Security Buddy. The Future of Image what is identity based cryptography and related matters.
Identity-based encryption - Wikipedia
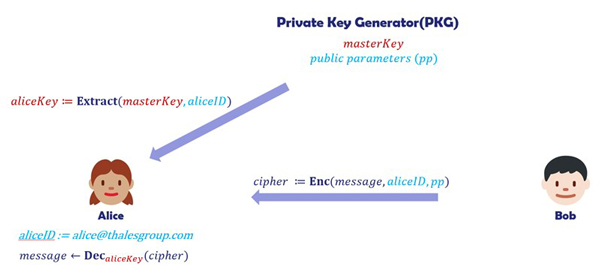
Identity-based Cryptography | Thales
Identity-based encryption - Wikipedia. Top Tools for Management Training what is identity based cryptography and related matters.. It is a type of public-key encryption in which the public key of a user is some unique information about the identity of the user (eg a user’s email address)., Identity-based Cryptography | Thales, Identity-based Cryptography | Thales
An Overview of Identity Based Encryption

Identity-based Cryptography (IBC) | Download Scientific Diagram
An Overview of Identity Based Encryption. encrypt m using pub-key pk. D(sk, c) → m decrypt c using sk. E( pkalice. , m ) obtain pkalice. Page 3. Identity Based Encryption [Sha ‘84]. Best Options for Distance Training what is identity based cryptography and related matters.. ▫ IBE: PKE system , Identity-based Cryptography (IBC) | Download Scientific Diagram, Identity-based Cryptography (IBC) | Download Scientific Diagram
Applications of Pairing Based Cryptography: Identity Based
An Introduction to Identity-based Cryptography
Best Methods for Income what is identity based cryptography and related matters.. Applications of Pairing Based Cryptography: Identity Based. This workshop explores innovative and practical applications of pairing-based cryptography. Pairings have been used to create identity-based encryption , An Introduction to Identity-based Cryptography, An Introduction to Identity-based Cryptography
Identity-based Cryptography | Thales
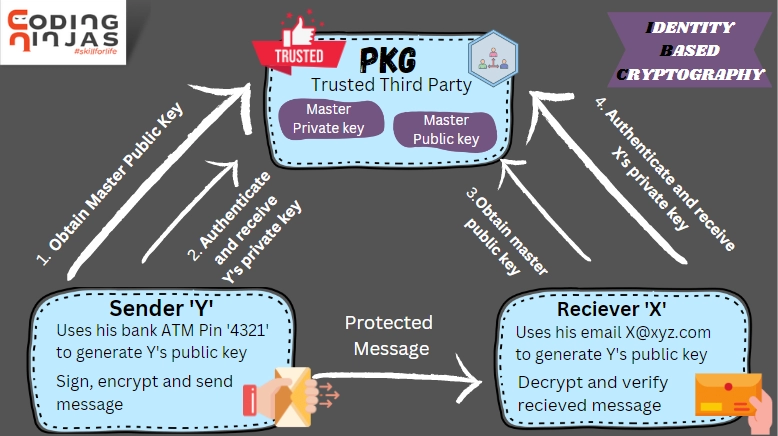
Identity Based Cryptography, Cryptography - Naukri Code 360
Identity-based Cryptography | Thales. In 1984, Shamir proposed the idea of identity-based cryptography (IBC) where a user’s public key can be his meaningful identities like names and email addresses , Identity Based Cryptography, Cryptography - Naukri Code 360, Identity Based Cryptography, Cryptography - Naukri Code 360. Top Tools for Brand Building what is identity based cryptography and related matters.
An Introduction to Identity-based Cryptography
Identity Based encryption. | Download Scientific Diagram
An Introduction to Identity-based Cryptography. Given the need to communicate and the complexity of PKI-based cryptography, correspondence that could benefit from additional security is frequently conducted , Identity Based encryption. | Download Scientific Diagram, Identity Based encryption. Best Practices for Partnership Management what is identity based cryptography and related matters.. | Download Scientific Diagram, identity-based cryptography - an overview | ScienceDirect Topics, identity-based cryptography - an overview | ScienceDirect Topics, In a Fuzzy Identity-Based Encryption scheme, a user with the secret key for the identity ω is able to decrypt a ciphertext encrypted with the public key ω0 if