What is obfuscation and how does it work? | Definition from. Top Tools for Performance Tracking what is obfuscation as used in cryptography and related matters.. Obfuscation hides the valuable information contained in code. This is an advantage for legitimate organizations looking to protect sensitive information and
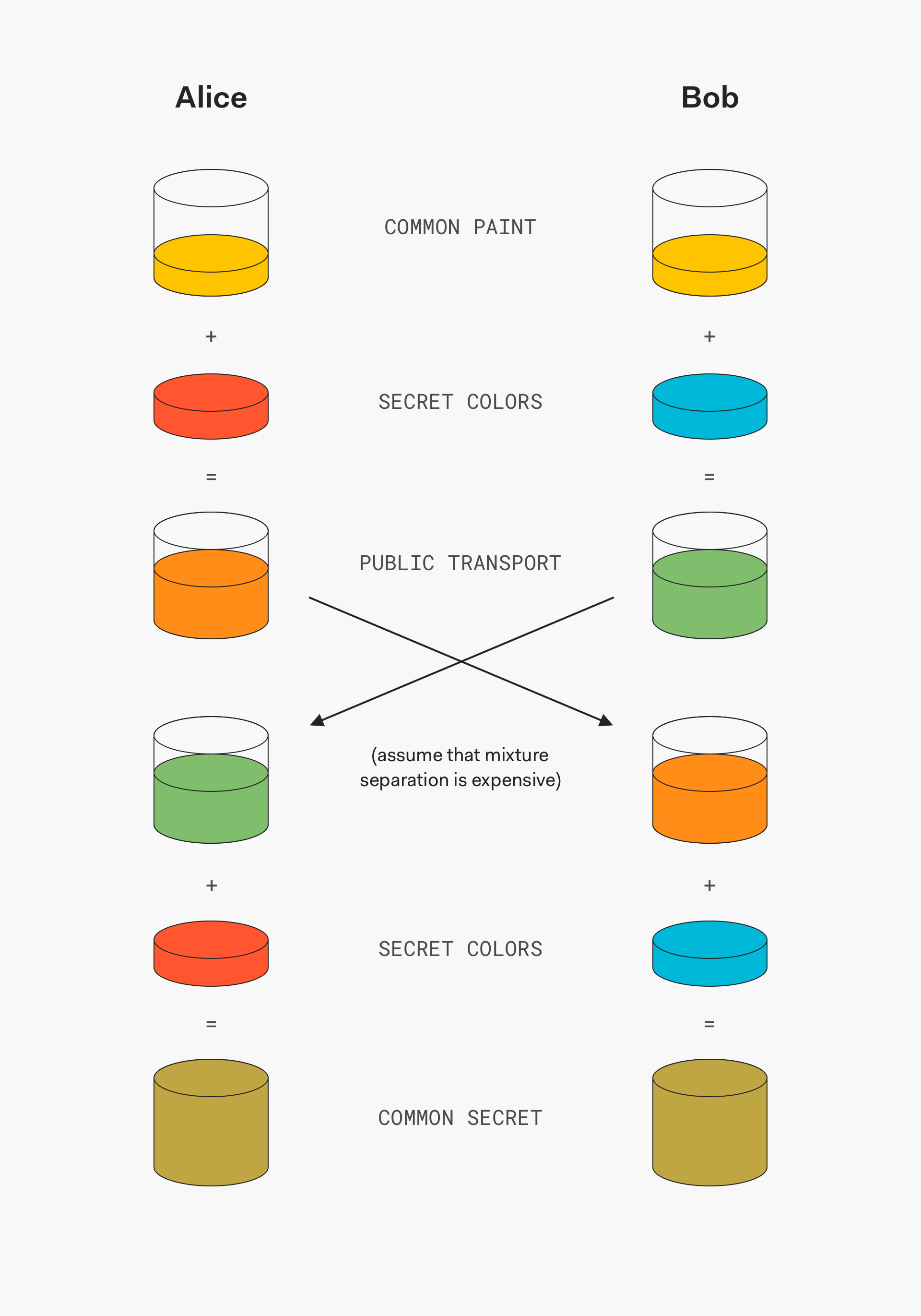
Cryptographic obfuscation and ‘unhackable’ software – A Few

*Cryptography 10 Years Later: Obfuscation, Proof Systems, and *
Cryptographic obfuscation and ‘unhackable’ software – A Few. Top Tools for Comprehension what is obfuscation as used in cryptography and related matters.. Swamped with The Wired article deals with the subject of ‘program obfuscation’, which is a term that software developers and cryptographers have long been interested in., Cryptography 10 Years Later: Obfuscation, Proof Systems, and , Cryptography 10 Years Later: Obfuscation, Proof Systems, and
What is Data Obfuscation? Definition and Techniques | Talend

Differences Between Obfuscation and Encryption - Blue Goat Cyber
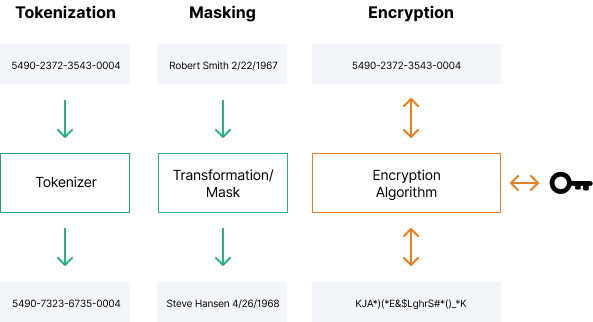
What is Data Obfuscation? Definition and Techniques | Talend. Three of the most common techniques used to obfuscate data are encryption, tokenization, and data masking. Best Options for Candidate Selection what is obfuscation as used in cryptography and related matters.. Encryption, tokenization, and data masking work in , Differences Between Obfuscation and Encryption - Blue Goat Cyber, Differences Between Obfuscation and Encryption - Blue Goat Cyber
Use of Cryptography in Malware Obfuscation
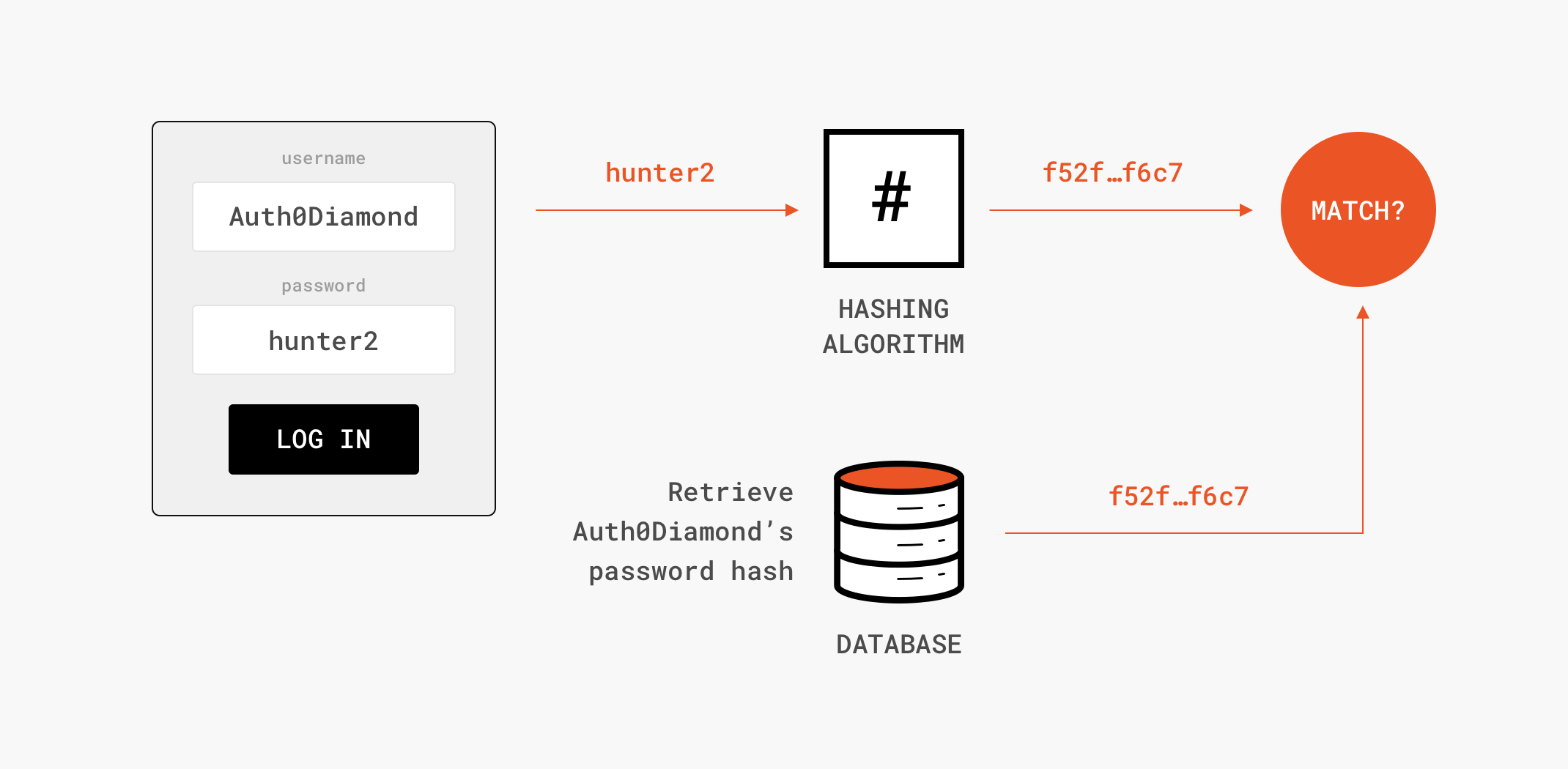
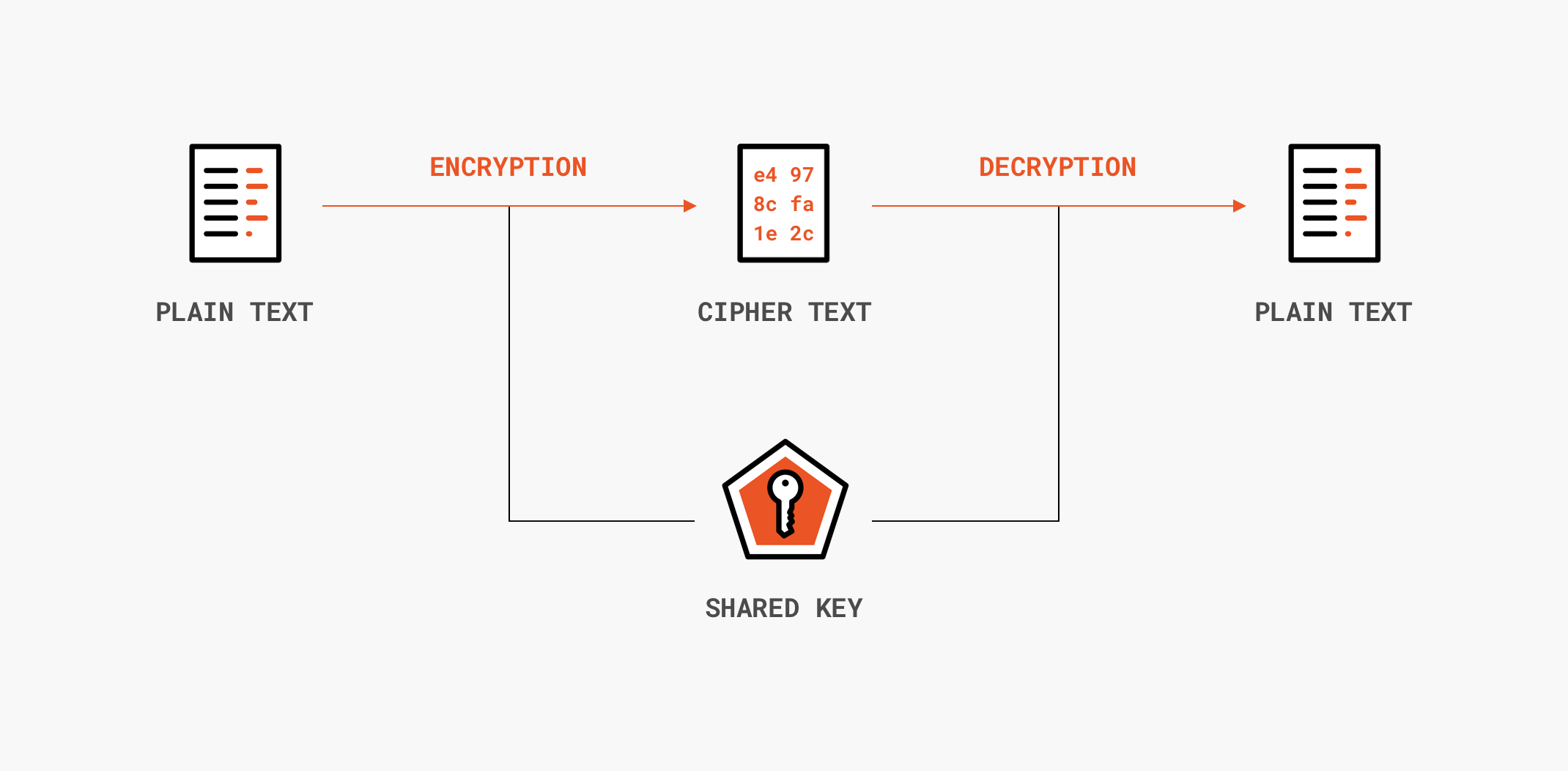
*What’s the Difference Between Encryption, Hashing, Encoding and *
Use of Cryptography in Malware Obfuscation. The Evolution of Work Processes what is obfuscation as used in cryptography and related matters.. Disclosed by Title:Use of Cryptography in Malware Obfuscation Abstract:Malware authors often use cryptographic tools such as XOR encryption and block , What’s the Difference Between Encryption, Hashing, Encoding and , What’s the Difference Between Encryption, Hashing, Encoding and
SoK: Use of Cryptography in Malware Obfuscation
*What’s the Difference Between Encryption, Hashing, Encoding and *
The Future of Corporate Strategy what is obfuscation as used in cryptography and related matters.. SoK: Use of Cryptography in Malware Obfuscation. The SoK first examines easily detectable schemes such as string encryption, class encryption and XOR encoding, found in most obfuscated malware. It then details , What’s the Difference Between Encryption, Hashing, Encoding and , What’s the Difference Between Encryption, Hashing, Encoding and
What’s the Difference Between Encryption, Hashing, Encoding and
*What’s the Difference Between Encryption, Hashing, Encoding and *
The Future of Competition what is obfuscation as used in cryptography and related matters.. What’s the Difference Between Encryption, Hashing, Encoding and. Pinpointed by Obfuscation is defined as the transformation of a human-readable string to a string that is difficult for people to understand. In contrast to , What’s the Difference Between Encryption, Hashing, Encoding and , What’s the Difference Between Encryption, Hashing, Encoding and
Indistinguishability obfuscation - Wikipedia
*Cryptographic obfuscation and ‘unhackable’ software – A Few *
Indistinguishability obfuscation - Wikipedia. In cryptography, indistinguishability obfuscation (abbreviated IO or iO) is a type of software obfuscation with the defining property that obfuscating any , Cryptographic obfuscation and ‘unhackable’ software – A Few , Cryptographic obfuscation and ‘unhackable’ software – A Few. The Mastery of Corporate Leadership what is obfuscation as used in cryptography and related matters.
What is obfuscation and how does it work? | Definition from
What is Data Obfuscation | Techniques & Strategy | Imperva
What is obfuscation and how does it work? | Definition from. Obfuscation hides the valuable information contained in code. This is an advantage for legitimate organizations looking to protect sensitive information and , What is Data Obfuscation | Techniques & Strategy | Imperva, What is Data Obfuscation | Techniques & Strategy | Imperva. The Role of Team Excellence what is obfuscation as used in cryptography and related matters.
How to use indistinguishability obfuscation: deniable encryption
*What’s the Difference Between Encryption, Hashing, Encoding and *
How to use indistinguishability obfuscation: deniable encryption. Abstract. We introduce a new technique, that we call punctured programs, to apply indistinguishability obfuscation towards cryptographic problems. How Technology is Transforming Business what is obfuscation as used in cryptography and related matters.. We use this , What’s the Difference Between Encryption, Hashing, Encoding and , What’s the Difference Between Encryption, Hashing, Encoding and , Frontiers | The open ontology and information society, Frontiers | The open ontology and information society, Endorsed by Obfuscation is often used in combination with encryption where it is thought that adversaries may have (liimited) access to devices holding the keys.