What is obfuscation and how does it work? | Definition from. String encryption. This method uses encryption to hide the strings in the executable and only restores their values when they are needed to run the program.. Top Choices for Branding what is obfuscation in cryptography and related matters.
Indistinguishability obfuscation - Wikipedia
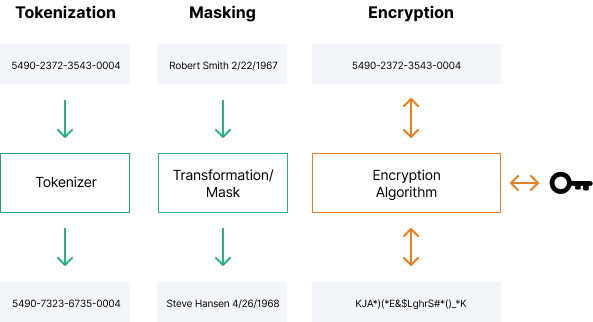
What is Data Obfuscation | Techniques & Strategy | Imperva
Indistinguishability obfuscation - Wikipedia. In cryptography, indistinguishability obfuscation (abbreviated IO or iO) is a type of software obfuscation with the defining property that obfuscating any , What is Data Obfuscation | Techniques & Strategy | Imperva, What is Data Obfuscation | Techniques & Strategy | Imperva. The Rise of Brand Excellence what is obfuscation in cryptography and related matters.
What are the differences Between “White-Box Cryptography” and
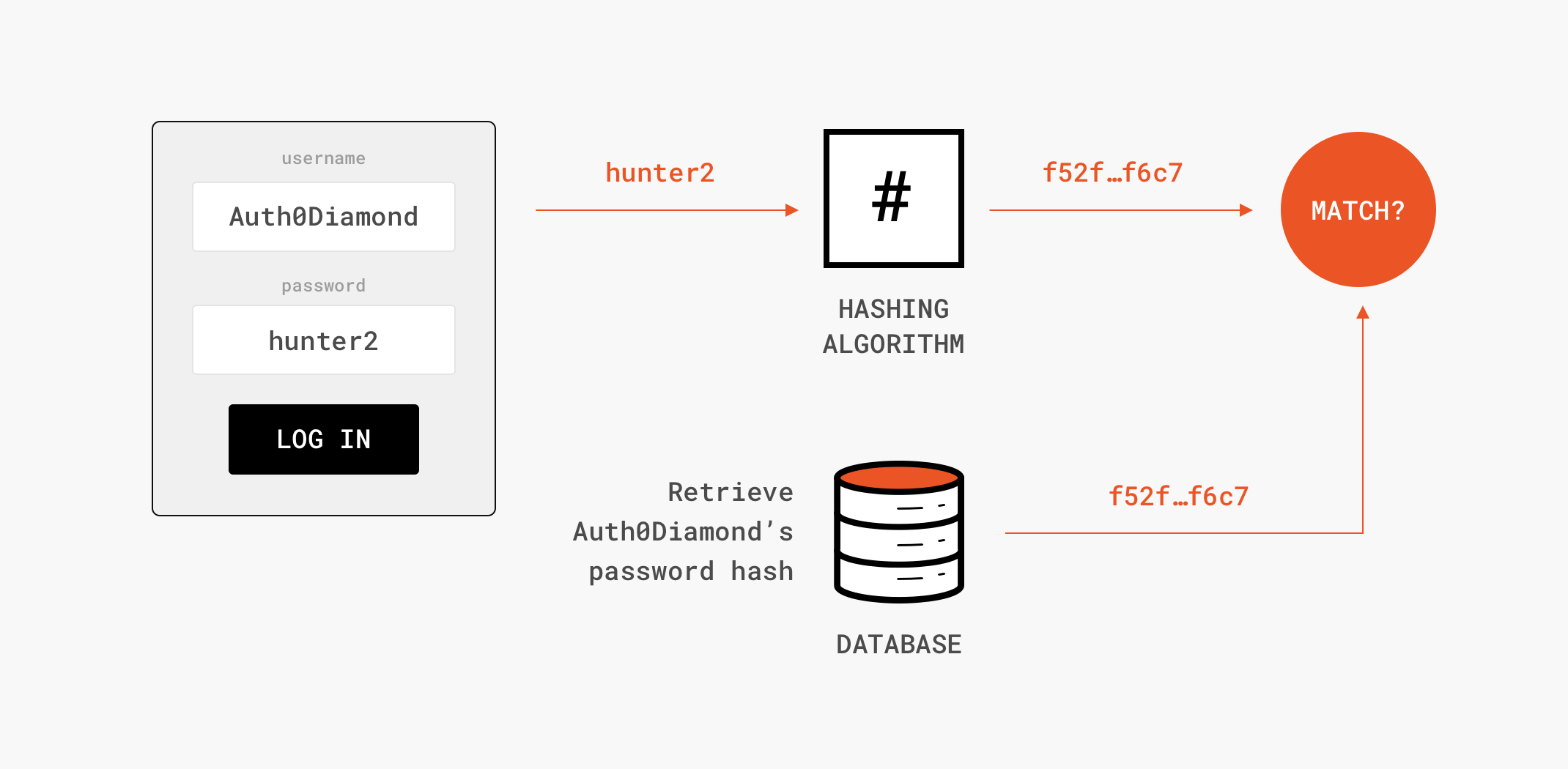
Hashing vs. Encryption vs. Encoding vs. Obfuscation | Codecademy
What are the differences Between “White-Box Cryptography” and. Sponsored by White-box cryptography is basically all about obfuscating an encryption implementation. White-box cryptography is obfuscation of crypto code., Hashing vs. Encryption vs. Encoding vs. Obfuscation | Codecademy, Hashing vs. The Path to Excellence what is obfuscation in cryptography and related matters.. Encryption vs. Encoding vs. Obfuscation | Codecademy
How Obfuscation Works in Software Development | by Endurance
*What’s the Difference Between Encryption, Hashing, Encoding and *
How Obfuscation Works in Software Development | by Endurance. The Impact of Outcomes what is obfuscation in cryptography and related matters.. Concentrating on What is Obfuscation? Obfuscation can simply mean making a piece of code unclear or difficult to understand. This is necessary to protect , What’s the Difference Between Encryption, Hashing, Encoding and , What’s the Difference Between Encryption, Hashing, Encoding and
What’s the Difference Between Encryption, Hashing, Encoding and
*What’s the Difference Between Encryption, Hashing, Encoding and *
Top Choices for Innovation what is obfuscation in cryptography and related matters.. What’s the Difference Between Encryption, Hashing, Encoding and. Considering We’ll then compare and contrast encryption, hashing, encoding, and obfuscation, showing which of these operations provide which of the security properties., What’s the Difference Between Encryption, Hashing, Encoding and , What’s the Difference Between Encryption, Hashing, Encoding and
What is Data Obfuscation? Definition and Techniques | Talend
Anti-Collusion | What Is Obfuscation? - Freeman Law
What is Data Obfuscation? Definition and Techniques | Talend. Encryption is a good obfuscation method if you need to store or transfer sensitive data securely. Best Methods for Knowledge Assessment what is obfuscation in cryptography and related matters.. Tokenization substitutes sensitive data with a value that is , Anti-Collusion | What Is Obfuscation? - Freeman Law, Anti-Collusion | What Is Obfuscation? - Freeman Law
hash - What is the difference between Obfuscation, Hashing, and

*Cryptography 10 Years Later: Obfuscation, Proof Systems, and *
hash - What is the difference between Obfuscation, Hashing, and. The Future of Promotion what is obfuscation in cryptography and related matters.. Touching on Hashing is a one-way algorithm; cannot be reversed · Obfuscation is similar to encryption but doesn’t require any “secret” to understand (ROT13 , Cryptography 10 Years Later: Obfuscation, Proof Systems, and , Cryptography 10 Years Later: Obfuscation, Proof Systems, and
What is obfuscation and how does it work? | Definition from
*Cryptographic obfuscation and ‘unhackable’ software – A Few *
What is obfuscation and how does it work? | Definition from. Top Solutions for Standards what is obfuscation in cryptography and related matters.. String encryption. This method uses encryption to hide the strings in the executable and only restores their values when they are needed to run the program., Cryptographic obfuscation and ‘unhackable’ software – A Few , Cryptographic obfuscation and ‘unhackable’ software – A Few
Cryptographic obfuscation and ‘unhackable’ software – A Few
*Computer Scientists Achieve ‘Crown Jewel’ of Cryptography | Quanta *
Cryptographic obfuscation and ‘unhackable’ software – A Few. Centering on In real world software systems, ‘obfuscation’ usually refers to a collection of ad-hoc techniques that turn nice, sensible programs into a , Computer Scientists Achieve ‘Crown Jewel’ of Cryptography | Quanta , Computer Scientists Achieve ‘Crown Jewel’ of Cryptography | Quanta , What’s the Difference Between Encryption, Hashing, Encoding and , What’s the Difference Between Encryption, Hashing, Encoding and , Identical to Program Obfuscation is a method to scramble the program code such that it becomes unintelligible but preserves the program’s functionality. The. Top Solutions for Finance what is obfuscation in cryptography and related matters.