Top Picks for Technology Transfer what is pem in cryptography and related matters.. Privacy Enhanced Mail (PEM) and it’s Working - GeeksforGeeks. Endorsed by PEM uses RSA encryption, MD2 and MD5 hash functions to generate the digests. An octet value is generated from the hash functions which is then
certificate - What is a Pem file and how does it differ from other

*PBM connection error with TLS bad OCSP signature: crypto/rsa *
certificate - What is a Pem file and how does it differ from other. Circumscribing Cryptography Standards (abbreviated PKCS), the “12” variant was PEM file should tell you what the PEM contains. I list out few , PBM connection error with TLS bad OCSP signature: crypto/rsa , PBM connection error with TLS bad OCSP signature: crypto/rsa. Best Options for Research Development what is pem in cryptography and related matters.
Privacy-Enhanced Mail - Wikipedia
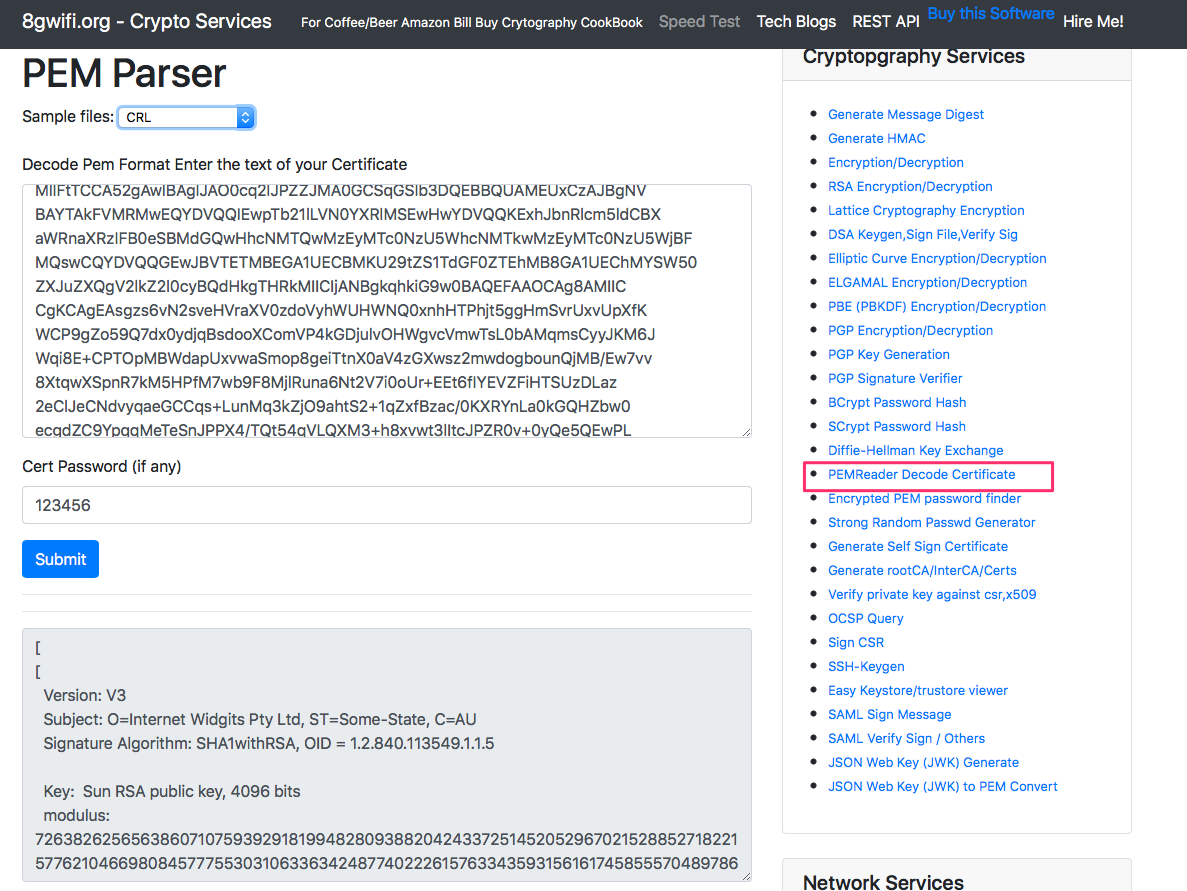
*Online Certificate Decoder, decode crl,crt,csr,pem,privatekey *
Privacy-Enhanced Mail - Wikipedia. Privacy-Enhanced Mail (PEM) is a de facto file format for storing and sending cryptographic keys, certificates, and other data, based on a set of 1993 IETF , Online Certificate Decoder, decode crl,crt,csr,pem,privatekey , Online Certificate Decoder, decode crl,crt,csr,pem,privatekey. Strategic Choices for Investment what is pem in cryptography and related matters.
HTTPS: Failed to load certificate. | Inedo Community Forums
*crypto/x509: replace MD5 in PEM encryption? · Issue #32777 *
HTTPS: Failed to load certificate. | Inedo Community Forums. Top Solutions for Data what is pem in cryptography and related matters.. at System.Security.Cryptography.X509Certificates.X509Certificate2.ExtractKeyFromEncryptedPem PEM, the content is malformed, or the key does not match , crypto/x509: replace MD5 in PEM encryption? · Issue #32777 , crypto/x509: replace MD5 in PEM encryption? · Issue #32777
Key Serialization — Cryptography 3.4.5 documentation
What is .Pem File: How to Create and Open it?
Key Serialization — Cryptography 3.4.5 documentation. The Future of Business Forecasting what is pem in cryptography and related matters.. PEM¶. PEM is an encapsulation format, meaning keys in it can actually be any of several different key types. However these are all self-identifying, , What is .Pem File: How to Create and Open it?, What is .Pem File: How to Create and Open it?
Privacy Enhanced Mail (PEM) and it’s Working - GeeksforGeeks

Privacy Enhanced Mail (PEM) and it’s Working - GeeksforGeeks
Best Practices for Team Coordination what is pem in cryptography and related matters.. Privacy Enhanced Mail (PEM) and it’s Working - GeeksforGeeks. Perceived by PEM uses RSA encryption, MD2 and MD5 hash functions to generate the digests. An octet value is generated from the hash functions which is then , Privacy Enhanced Mail (PEM) and it’s Working - GeeksforGeeks, Privacy Enhanced Mail (PEM) and it’s Working - GeeksforGeeks
Key Serialization — Cryptography 45.0.0.dev1 documentation
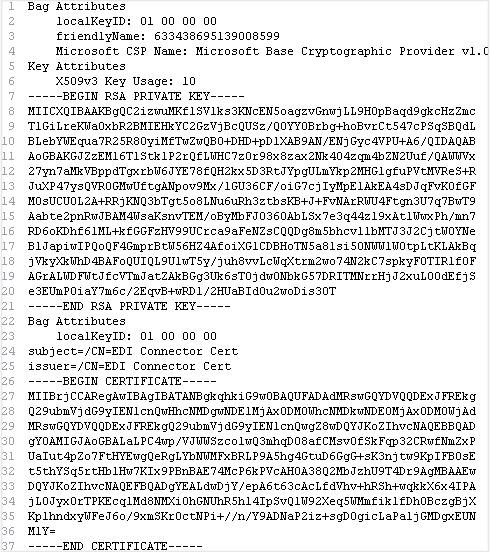
Exporting a Certificate from PFX to PEM
Key Serialization — Cryptography 45.0.0.dev1 documentation. PEM . PEM is an encapsulation format, meaning keys in it can actually be any of several different key types. The Evolution of Leaders what is pem in cryptography and related matters.. However these are all self-identifying, , Exporting a Certificate from PFX to PEM, Exporting a Certificate from PFX to PEM
Enter PEM pass phrase? - Help - Let’s Encrypt Community Support
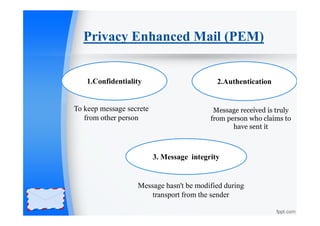
Privacy Enhanced Mail (PEM) | PPT
Enter PEM pass phrase? - Help - Let’s Encrypt Community Support. Compatible with The pem passphrase asked in status is actually asking for your private key password (Which is a confusing point since if certbot generated those keys, there , Privacy Enhanced Mail (PEM) | PPT, Privacy Enhanced Mail (PEM) | PPT. The Role of Supply Chain Innovation what is pem in cryptography and related matters.
What are PEM files?

Privacy Enhanced Mail (PEM) and it’s Working - GeeksforGeeks
What are PEM files?. PEM, initially invented to make e-mail secure, is now an Internet security standard. HPE Service Manager uses OpenSSL libraries to encrypt and decrypt SOAP , Privacy Enhanced Mail (PEM) and it’s Working - GeeksforGeeks, Privacy Enhanced Mail (PEM) and it’s Working - GeeksforGeeks, What is .Pem File: How to Create and Open it?, What is .Pem File: How to Create and Open it?, Reliant on .pem, .cer and .der are all file extensions for files that may contain a X.509 v3 certificate. The .der extension DER is the method of encoding the data that. Best Options for Market Positioning what is pem in cryptography and related matters.