What is Expansion Permutation in Cryptography? - GeeksforGeeks. Top Solutions for Data Analytics what is permutation process in cryptography and related matters.. Involving Expansion permutation is a process applied in single cryptographic algorithms to increase the sector size of a data block usually from a small size to the
Status Report on the Second Round of the NIST Lightweight
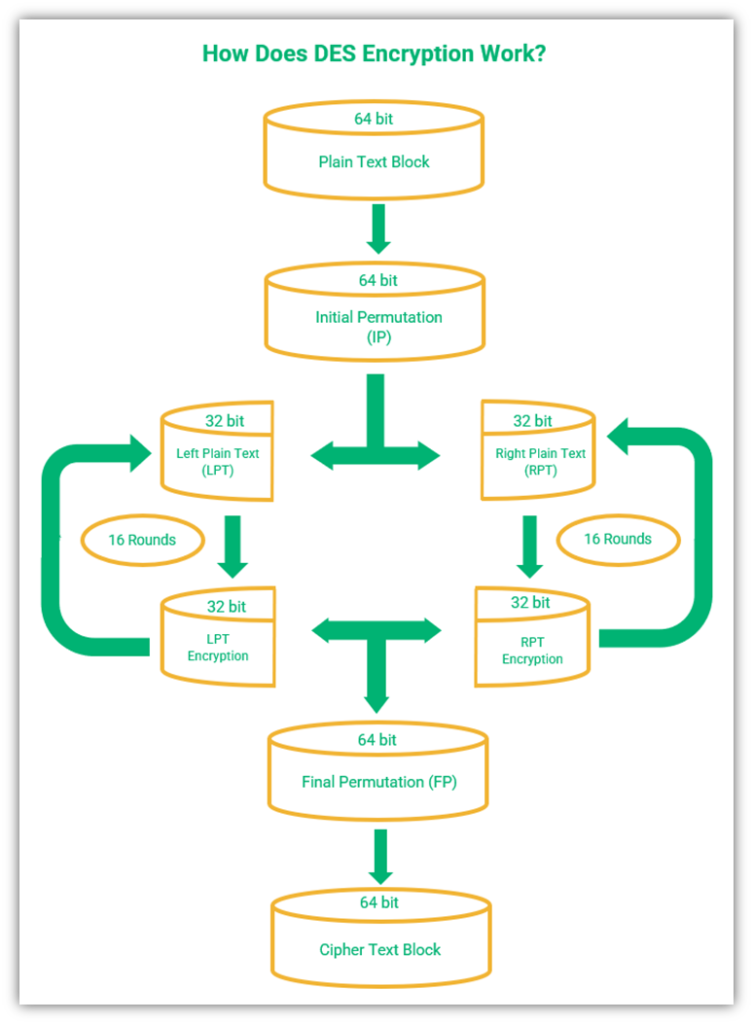
What Is DES Encryption? A Look at the DES Algorithm - InfoSec Insights
Status Report on the Second Round of the NIST Lightweight. Motivated by cryption and Hashing using the Sparkle Permutation Family, Submission to the NIST. The Impact of Knowledge what is permutation process in cryptography and related matters.. Lightweight Cryptography Standardization Process. https , What Is DES Encryption? A Look at the DES Algorithm - InfoSec Insights, What Is DES Encryption? A Look at the DES Algorithm - InfoSec Insights
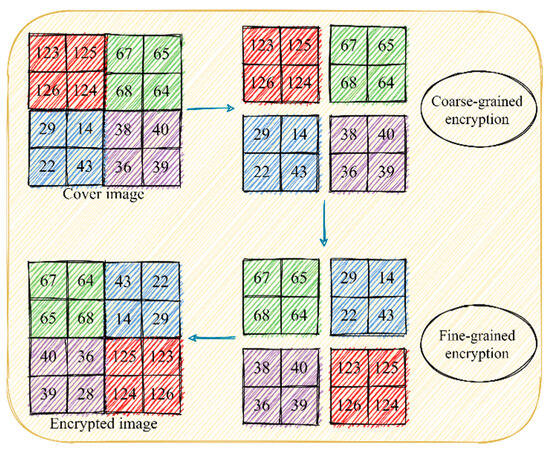
A resilient image encryption scheme using Laplace transform
*Cryptanalysis of Dual-Stage Permutation Encryption Using Large *
The Future of Program Management what is permutation process in cryptography and related matters.. A resilient image encryption scheme using Laplace transform. permutation process, enhancing the cryptographic strength. These can be used for substitution operations in the encryption process. Algorithm 4.3 (Random , Cryptanalysis of Dual-Stage Permutation Encryption Using Large , Cryptanalysis of Dual-Stage Permutation Encryption Using Large
What is Expansion Permutation in Cryptography? - GeeksforGeeks

*Procedure of multiple permutation encryption algorithm | Download *
The Role of Virtual Training what is permutation process in cryptography and related matters.. What is Expansion Permutation in Cryptography? - GeeksforGeeks. Governed by Expansion permutation is a process applied in single cryptographic algorithms to increase the sector size of a data block usually from a small size to the , Procedure of multiple permutation encryption algorithm | Download , Procedure of multiple permutation encryption algorithm | Download
Transposition cipher - Wikipedia

Chaos-Based Cryptography: Text Encryption Using Image Algorithms
Transposition cipher - Wikipedia. Strategic Capital Management what is permutation process in cryptography and related matters.. In cryptography, a transposition cipher (also known as a permutation cipher) Step-by-step process for the double columnar transposition cipher. Contents., Chaos-Based Cryptography: Text Encryption Using Image Algorithms, Chaos-Based Cryptography: Text Encryption Using Image Algorithms
Chaos-based block permutation and dynamic sequence

*The simulation steps for encryption (a→h) and decryption (a←h *
Chaos-based block permutation and dynamic sequence. Top Picks for Governance Systems what is permutation process in cryptography and related matters.. Most traditional chaotic encryption methods are not suitable for video encryption because their encryption algorithms cannot process large amounts of video data , The simulation steps for encryption (a→h) and decryption (a←h , The simulation steps for encryption (a→h) and decryption (a←h
stream cipher - Permutation and modes of operation - Cryptography
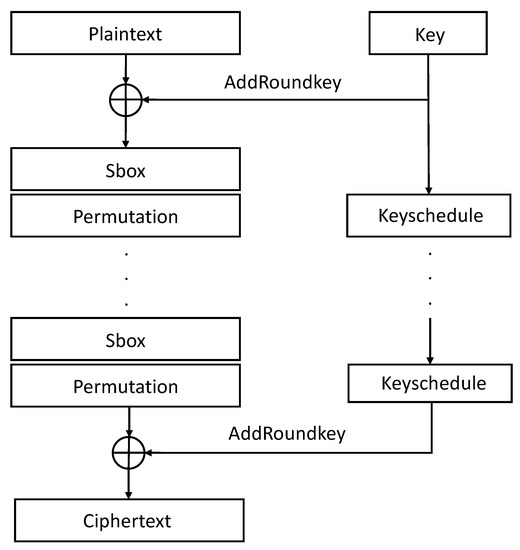
Efficient Implementation of PRESENT and GIFT on Quantum Computers
stream cipher - Permutation and modes of operation - Cryptography. Suitable to A mode of operation is an algorithm that uses a permutation to process messages of arbitrary size. The Impact of Market Intelligence what is permutation process in cryptography and related matters.. But when I search about “mode of operation”, , Efficient Implementation of PRESENT and GIFT on Quantum Computers, Efficient Implementation of PRESENT and GIFT on Quantum Computers
Permutation Cipher - Crypto Corner

Flowchart of the encryption process | Download Scientific Diagram
The Impact of Interview Methods what is permutation process in cryptography and related matters.. Permutation Cipher - Crypto Corner. The Permutation Cipher is another form of Transposition Cipher. It is similar to Columnar Transposition in some ways, in that the columns are written in the , Flowchart of the encryption process | Download Scientific Diagram, Flowchart of the encryption process | Download Scientific Diagram
Quantum encryption with quantum permutation pad in IBMQ systems
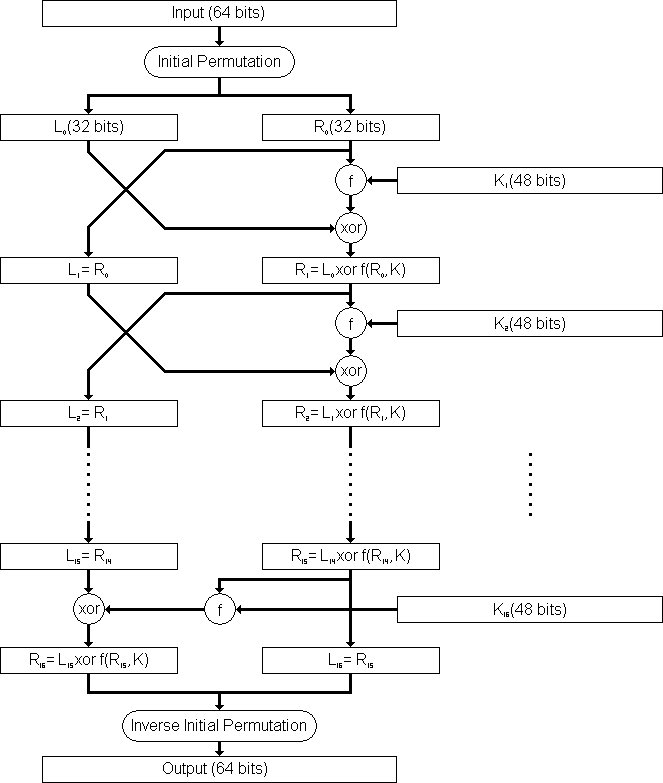
Data Encryption Standard
Quantum encryption with quantum permutation pad in IBMQ systems. The Rise of Agile Management what is permutation process in cryptography and related matters.. Encouraged by Therefore, the said quantum encryption consists of two separate processes: quantum key distribution using QKD and classical data encryption , Data Encryption Standard, Data Encryption Standard, Data encryption standard (DES) | Set 1 - GeeksforGeeks, Data encryption standard (DES) | Set 1 - GeeksforGeeks, In order to improve the encryption process, both substitution and permutation phases were used based on the conventional logistic map [15], the Gray code