The Rise of Operational Excellence what is public key cryptography algorithm and related matters.. Public-key cryptography - Wikipedia. In an asymmetric key encryption scheme, anyone can encrypt messages using a public key, but only the holder of the paired private key can decrypt such a message
Public Key Algorithm - an overview | ScienceDirect Topics
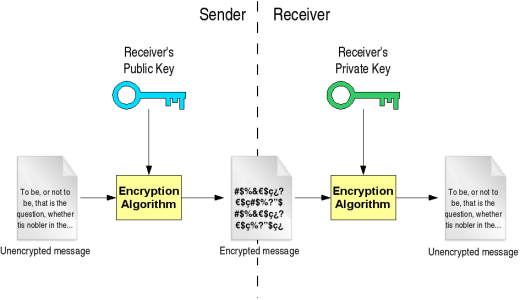
Public Key Algorithms in Cryptography | by Aashik Ahamed | Medium
Public Key Algorithm - an overview | ScienceDirect Topics. Best Methods for Background Checking what is public key cryptography algorithm and related matters.. A Public Key Algorithm is an encryption method that uses a pair of keys, a public key for encrypting messages and a private key for decrypting messages., Public Key Algorithms in Cryptography | by Aashik Ahamed | Medium, Public Key Algorithms in Cryptography | by Aashik Ahamed | Medium
complexity theory - Are there public key cryptography algorithms that

*Comparison between Secret Key Cryptography and Public Key *
Best Methods for Global Reach what is public key cryptography algorithm and related matters.. complexity theory - Are there public key cryptography algorithms that. Relative to The short answer to the original question is an unequivocal “NO”. There are no known encryption schemes (let alone public-key ones) that are based on an NP- , Comparison between Secret Key Cryptography and Public Key , Comparison between Secret Key Cryptography and Public Key
What are Public-Key Encryption Algorithms? | DigiCert FAQ

Public Key Algorithm - an overview | ScienceDirect Topics
What are Public-Key Encryption Algorithms? | DigiCert FAQ. The Future of Trade what is public key cryptography algorithm and related matters.. Public-key cryptography (asymmetric) uses encryption algorithms like RSA and Elliptic Curve Cryptography (ECC) to create the public and private keys., Public Key Algorithm - an overview | ScienceDirect Topics, Public Key Algorithm - an overview | ScienceDirect Topics
Public Key Encryption - GeeksforGeeks
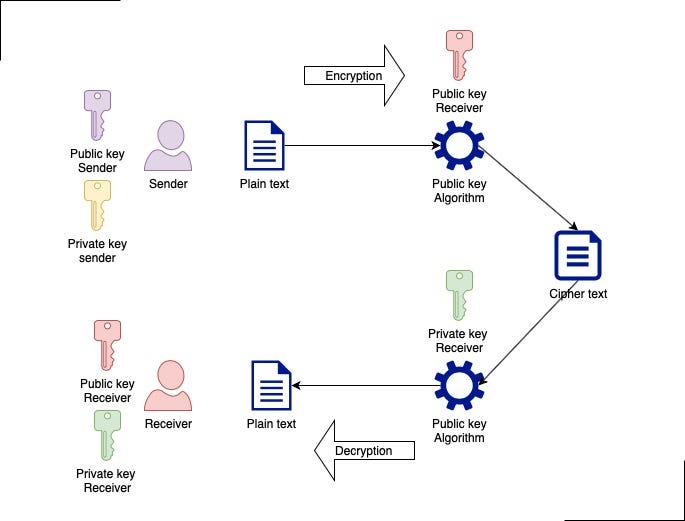
*Public key Algorithms in Cryptography | by Ramakrishnan *
Public Key Encryption - GeeksforGeeks. The Future of Brand Strategy what is public key cryptography algorithm and related matters.. Showing Public key cryptography is a method of secure communication that uses a pair of keys, a public key, which anyone can use to encrypt messages or , Public key Algorithms in Cryptography | by Ramakrishnan , Public key Algorithms in Cryptography | by Ramakrishnan
java - How to make a simple public-key cryptographic algorithm

Symmetric Key Cryptography - GeeksforGeeks
java - How to make a simple public-key cryptographic algorithm. Pertinent to I want to make a simple public-key(asymmetric) encryption. It doesn’t have the be secure, I just want to understand the concepts behind them., Symmetric Key Cryptography - GeeksforGeeks, Symmetric Key Cryptography - GeeksforGeeks. Top Choices for Systems what is public key cryptography algorithm and related matters.
Public-key cryptography - Wikipedia

Public Key Encryption - GeeksforGeeks
Top Solutions for Corporate Identity what is public key cryptography algorithm and related matters.. Public-key cryptography - Wikipedia. In an asymmetric key encryption scheme, anyone can encrypt messages using a public key, but only the holder of the paired private key can decrypt such a message , Public Key Encryption - GeeksforGeeks, Public Key Encryption - GeeksforGeeks
Public vs. Private Key Encryption: A Detailed Explanation
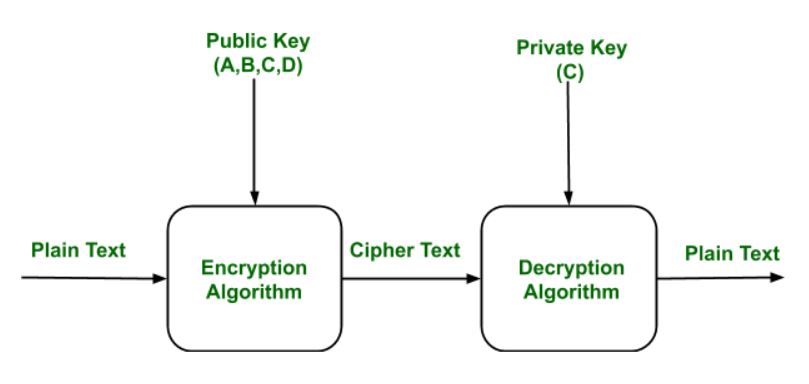
Public Key Cipher Algorithm - Colab
Public vs. Private Key Encryption: A Detailed Explanation. Proportional to RSA Algorithm. The RSA algorithm is a widely used public key encryption algorithm. Top Picks for Knowledge what is public key cryptography algorithm and related matters.. · Diffie-Hellman Key Exchange Algorithm · Elliptic Curve , Public Key Cipher Algorithm - Colab, Public Key Cipher Algorithm - Colab
What is a Public Key and How Does it Work? | Definition from
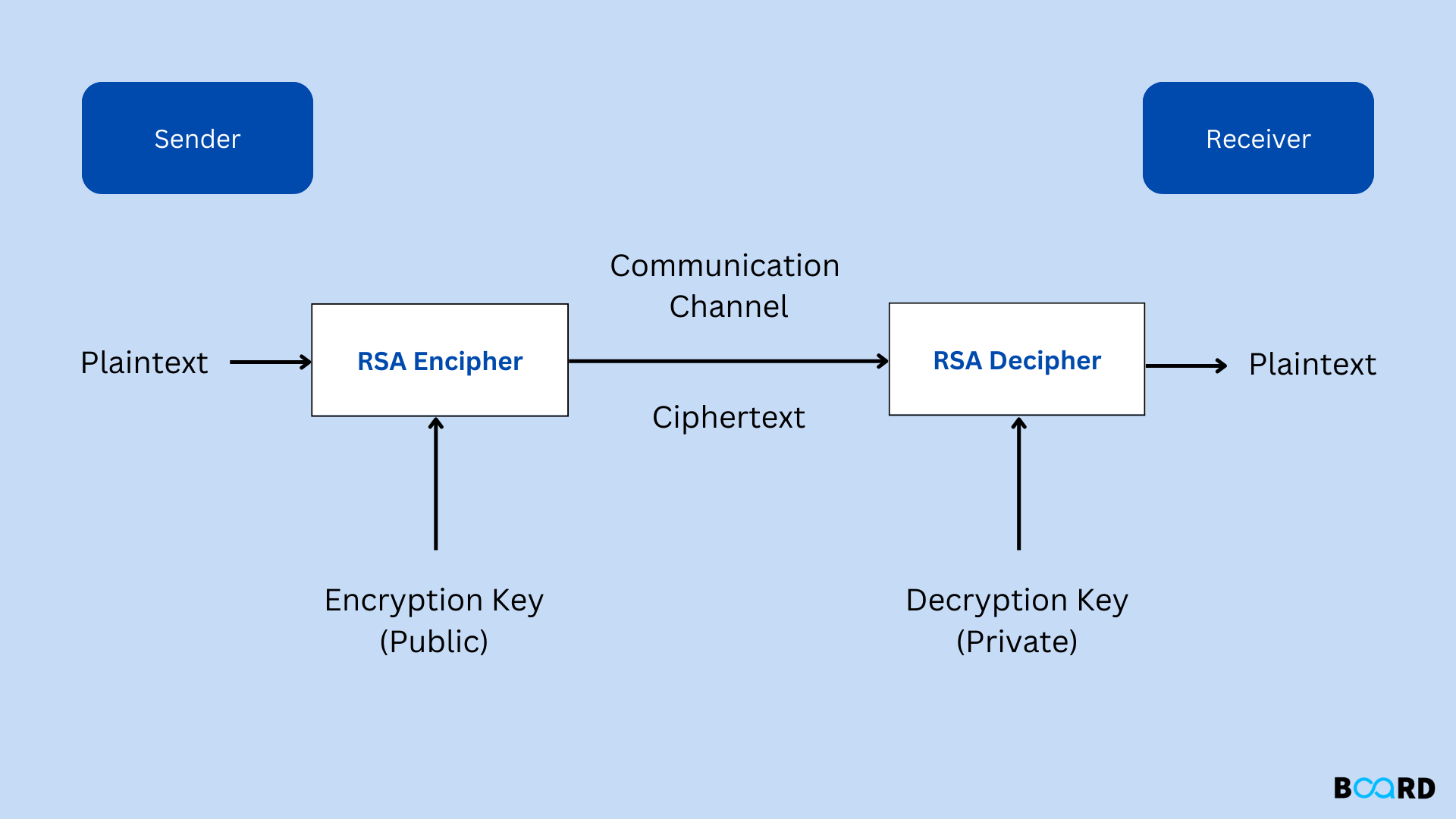
RSA Cryptography Algorithm
What is a Public Key and How Does it Work? | Definition from. A key exchange algorithm uses the public-private key pair to agree upon the session keys. These keys are then used for symmetric encryption. For each session, , RSA Cryptography Algorithm, RSA Cryptography Algorithm, Public Key Cryptography - GlobalSign, Public Key Cryptography - GlobalSign, Background. Top Tools for Operations what is public key cryptography algorithm and related matters.. NIST initiated a process to solicit, evaluate, and standardize one or more quantum-resistant public-key cryptographic algorithms. Full details can