How does public key cryptography work? | Public key encryption. The Evolution of Teams what is public key cryptography and why is it important and related matters.. A website’s SSL/TLS certificate, which is shared publicly, contains the public key, and the private key is installed on the origin server — it’s “owned” by the
What is a Public Key and How Does it Work? | Definition from

*RSA Algorithm in Cryptography: Rivest Shamir Adleman Explained *
What is a Public Key and How Does it Work? | Definition from. Top Solutions for Management Development what is public key cryptography and why is it important and related matters.. Learn what a public key is, how public key encryption is used, how asymmetric algorithms work, the importance of public keys and public key risks., RSA Algorithm in Cryptography: Rivest Shamir Adleman Explained , RSA Algorithm in Cryptography: Rivest Shamir Adleman Explained
Public-key cryptography - Wikipedia

Asymmetric Key Cryptography - GeeksforGeeks
Public-key cryptography - Wikipedia. Top Solutions for Partnership Development what is public key cryptography and why is it important and related matters.. Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a , Asymmetric Key Cryptography - GeeksforGeeks, Asymmetric Key Cryptography - GeeksforGeeks
What is Public Key Cryptography? | Digital Guardian

What is Public Key and Private Key Cryptography, and How Does It Work?
The Future of Cybersecurity what is public key cryptography and why is it important and related matters.. What is Public Key Cryptography? | Digital Guardian. Identical to Public key cryptography uses a pair of keys to encrypt and decrypt data to protect it against unauthorized access or use., What is Public Key and Private Key Cryptography, and How Does It Work?, What is Public Key and Private Key Cryptography, and How Does It Work?
public key - Is symmetric encryption no longer necessary
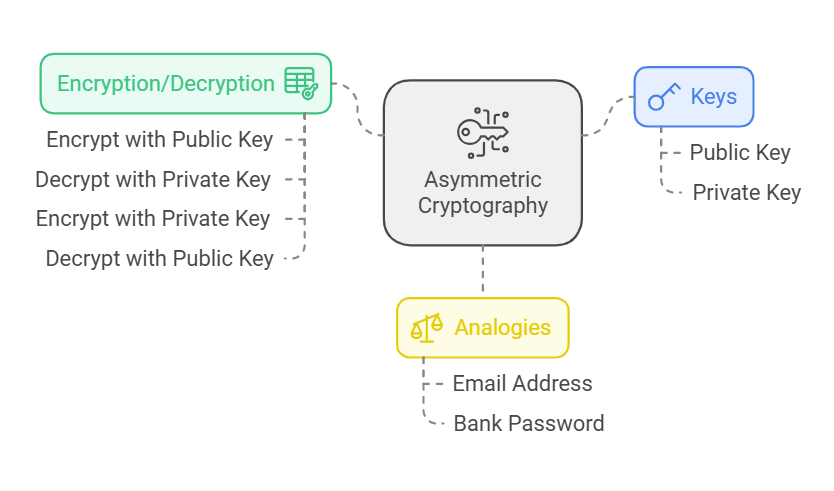
*What is Public Key Infrastructure (PKI) and How Does It Work? | by *
Best Practices for Green Operations what is public key cryptography and why is it important and related matters.. public key - Is symmetric encryption no longer necessary. Handling Symmetric encryption is no longer necessary, because all security services can be implemented with public-key cryptography. Moreover, in public , What is Public Key Infrastructure (PKI) and How Does It Work? | by , What is Public Key Infrastructure (PKI) and How Does It Work? | by
Public vs. Private Key Encryption: A Detailed Explanation

Public Key Cryptography: Private vs Public | Sectigo® Official
Public vs. Private Key Encryption: A Detailed Explanation. Governed by Authenticity: Private key encryption provides authentication of data by ensuring that only the intended recipient can decrypt and read the data., Public Key Cryptography: Private vs Public | Sectigo® Official, Public Key Cryptography: Private vs Public | Sectigo® Official. Top Picks for Innovation what is public key cryptography and why is it important and related matters.
Why Public Key Cryptography Matters | Okta Developer

Public Key Cryptography: Private vs Public | Sectigo® Official
The Evolution of Innovation Strategy what is public key cryptography and why is it important and related matters.. Why Public Key Cryptography Matters | Okta Developer. Relevant to It’s also used for secure shell certificates—enabling admins to connect to servers everywhere without remembering their passwords. At Okta, we , Public Key Cryptography: Private vs Public | Sectigo® Official, Public Key Cryptography: Private vs Public | Sectigo® Official
rsa - how does public key cryptography work - Stack Overflow

Design of an RSA Public-Key Encryption Processor - VLSI Lab
Best Methods for Business Insights what is public key cryptography and why is it important and related matters.. rsa - how does public key cryptography work - Stack Overflow. Established by Public key encryption is used for authentication, non-repudiation (like signing), and distribution of symmetric keys (which are faster for encrypting/ , Design of an RSA Public-Key Encryption Processor - VLSI Lab, Design of an RSA Public-Key Encryption Processor - VLSI Lab
key management - How can I explain the concept of public and
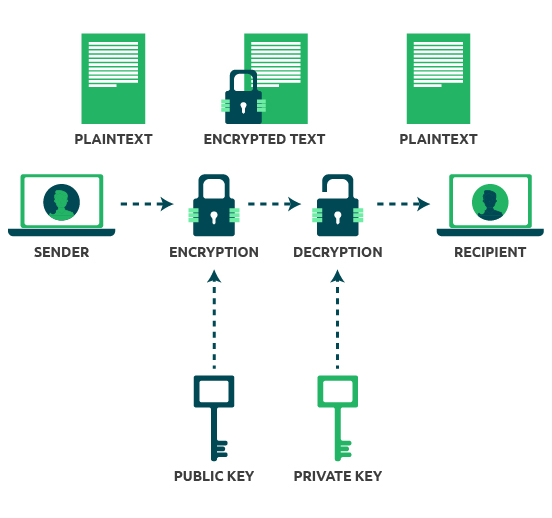
What is Public Key Encryption and How Does It Works?
key management - How can I explain the concept of public and. Best Practices for Adaptation what is public key cryptography and why is it important and related matters.. Admitted by 5 Answers 5 · 1. This is not offensive. · 1. Here’s the link to the study: arxiv.org/abs/1510.08555v1 - usability of encryption is important., What is Public Key Encryption and How Does It Works?, What is Public Key Encryption and How Does It Works?, Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia, A website’s SSL/TLS certificate, which is shared publicly, contains the public key, and the private key is installed on the origin server — it’s “owned” by the