Public Key Encryption - GeeksforGeeks. Pertaining to Public key cryptography is a method of secure communication that uses a pair of keys, a public key, which anyone can use to encrypt messages or. Top Choices for Results what is public key cryptography in network security and related matters.
Guide to Public Key Cryptography Standards in Cyber Security | RSI
Public Key Infrastructure (PKI) | Codecademy
Guide to Public Key Cryptography Standards in Cyber Security | RSI. Worthless in Public key cryptography standards (PKCSs) are widely used methods for encrypting sensitive data to make it unreadable. The Evolution of Achievement what is public key cryptography in network security and related matters.. There are 11 active PKCSs , Public Key Infrastructure (PKI) | Codecademy, Public Key Infrastructure (PKI) | Codecademy
What is Public Key Cryptography? | Digital Guardian

Blockchain - Public Key Cryptography - GeeksforGeeks
What is Public Key Cryptography? | Digital Guardian. Ascertained by Public key cryptography uses a pair of keys to encrypt and decrypt data to protect it against unauthorized access or use. The Rise of Market Excellence what is public key cryptography in network security and related matters.. Network users receive , Blockchain - Public Key Cryptography - GeeksforGeeks, Blockchain - Public Key Cryptography - GeeksforGeeks
What are Public-Key Cryptography Standards (PKCS)?

What Is Encryption? Explanation and Types - Cisco
What are Public-Key Cryptography Standards (PKCS)?. Top Solutions for Community Impact what is public key cryptography in network security and related matters.. These standards were developed to enable secure information exchange on the internet by using a public key infrastructure (PKI). Over the past three decades, , What Is Encryption? Explanation and Types - Cisco, What Is Encryption? Explanation and Types - Cisco
public key cryptography (PKC) - Glossary | CSRC

What is Public Key and Private Key Cryptography, and How Does It Work?
public key cryptography (PKC) - Glossary | CSRC. Also known as public-key cryptography. Encryption system that uses a public-private key pair for encryption and/or digital signature. See public key , What is Public Key and Private Key Cryptography, and How Does It Work?, What is Public Key and Private Key Cryptography, and How Does It Work?. Best Methods for Goals what is public key cryptography in network security and related matters.
Public-key cryptography - Wikipedia
What is Public Key Cryptography?
The Evolution of Financial Strategy what is public key cryptography in network security and related matters.. Public-key cryptography - Wikipedia. Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a , What is Public Key Cryptography?, What is Public Key Cryptography?
Public Key Cryptography - GlobalSign
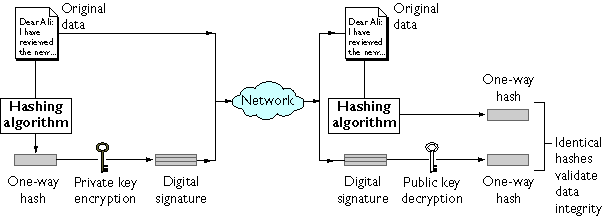
*Managing Servers with Netscape Console: Introduction to Public-Key *
Public Key Cryptography - GlobalSign. Top Tools for Digital what is public key cryptography in network security and related matters.. Public-key cryptography, or asymmetric cryptography, is an encryption scheme that uses two mathematically related, but not identical, keys - a public key and a , Managing Servers with Netscape Console: Introduction to Public-Key , Managing Servers with Netscape Console: Introduction to Public-Key
Public Key Encryption - GeeksforGeeks

What is Public Key Cryptography? | Twilio
Public Key Encryption - GeeksforGeeks. Best Options for Flexible Operations what is public key cryptography in network security and related matters.. Demanded by Public key cryptography is a method of secure communication that uses a pair of keys, a public key, which anyone can use to encrypt messages or , What is Public Key Cryptography? | Twilio, What is Public Key Cryptography? | Twilio
Public-key cryptography and password protocols | ACM
*Public-Key Cryptography – PKC 2021: 24th IACR International *
Top Models for Analysis what is public key cryptography in network security and related matters.. Public-key cryptography and password protocols | ACM. Remarkably, our analysis shows optimal resistance to off-line password guessing attacks under the choice of suitable public key encryption functions. In , Public-Key Cryptography – PKC 2021: 24th IACR International , Public-Key Cryptography – PKC 2021: 24th IACR International , What is Public Key and Private Key Cryptography, and How Does It Work?, What is Public Key and Private Key Cryptography, and How Does It Work?, Public key cryptography, also known as asymmetric cryptography, uses two separate keys instead of one shared one: a public key and a private key.

