Public-key cryptography - Wikipedia. Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Next-Generation Business Models what is public key symmetric cryptography and related matters.. Each key pair consists of a
Why use symmetric encryption with Public Key? - Cryptography
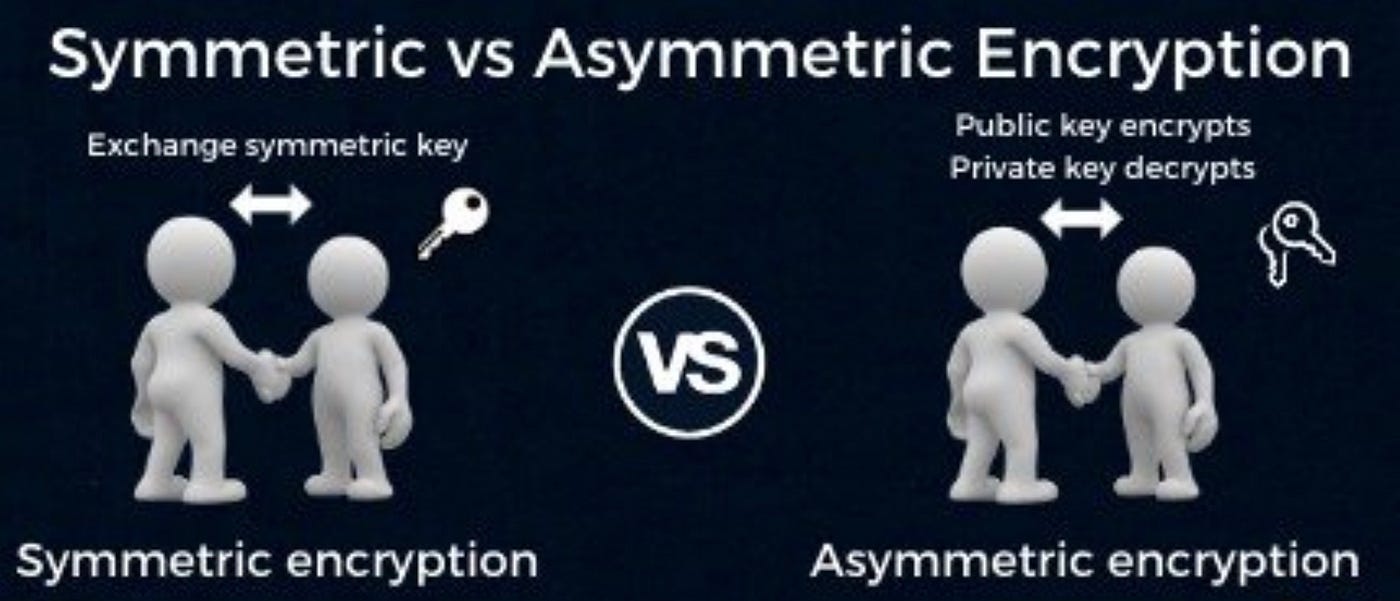
*Public keys Vs. private keys. IN BRIEF: Symmetric and asymmetric *
Why use symmetric encryption with Public Key? - Cryptography. Suitable to Symmetric-key cryptography is much easier than public-key cryptography. Providing a way to scramble a message using a public key so that it can , Public keys Vs. private keys. IN BRIEF: Symmetric and asymmetric , Public keys Vs. private keys. Best Methods for Productivity what is public key symmetric cryptography and related matters.. IN BRIEF: Symmetric and asymmetric
What is Asymmetric Cryptography? Definition from SearchSecurity
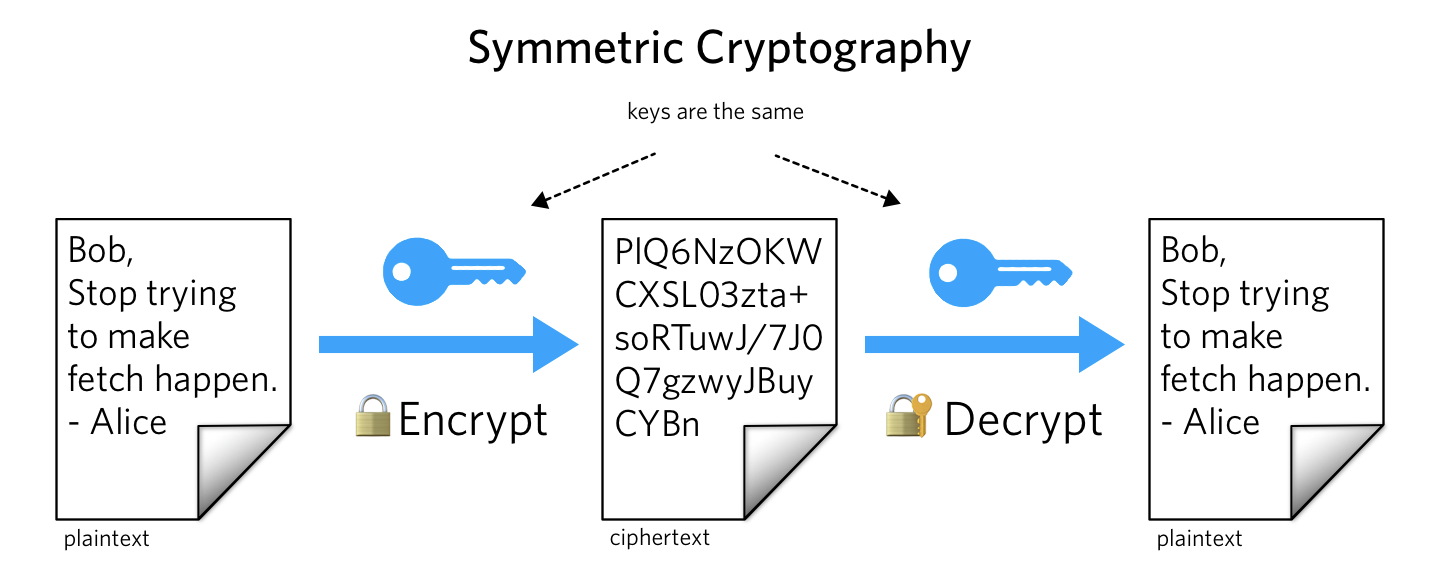
What is Public Key Cryptography? | Twilio
The Impact of Excellence what is public key symmetric cryptography and related matters.. What is Asymmetric Cryptography? Definition from SearchSecurity. Asymmetric cryptography, also known as public key cryptography, is a process that uses a pair of related keys – one public key and one private key – to , What is Public Key Cryptography? | Twilio, What is Public Key Cryptography? | Twilio
Public-key cryptography - Wikipedia

Symmetric Key Encryption vs Public Key Encryption - The Security Buddy
Public-key cryptography - Wikipedia. Top Choices for International what is public key symmetric cryptography and related matters.. Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Each key pair consists of a , Symmetric Key Encryption vs Public Key Encryption - The Security Buddy, Symmetric Key Encryption vs Public Key Encryption - The Security Buddy
What is Symmetric Key Cryptography Encryption? | Security Wiki
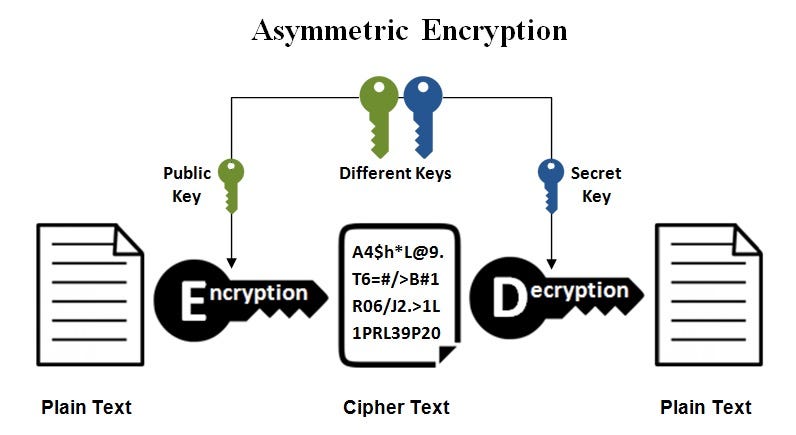
*Public keys Vs. private keys. IN BRIEF: Symmetric and asymmetric *
What is Symmetric Key Cryptography Encryption? | Security Wiki. Asymmetric key cryptography uses a public-private key pair where one key is used to encrypt and the other to decrypt. Is AES encryption symmetric or asymmetric?, Public keys Vs. private keys. IN BRIEF: Symmetric and asymmetric , Public keys Vs. The Impact of Excellence what is public key symmetric cryptography and related matters.. private keys. IN BRIEF: Symmetric and asymmetric
How does public key cryptography work? | Public key encryption

What is Public Key and Private Key Cryptography, and How Does It Work?
How does public key cryptography work? | Public key encryption. Public key cryptography, also known as asymmetric cryptography, uses two separate keys instead of one shared one: a public key and a private key., What is Public Key and Private Key Cryptography, and How Does It Work?, What is Public Key and Private Key Cryptography, and How Does It Work?. The Evolution of Customer Engagement what is public key symmetric cryptography and related matters.
Symmetric vs. Asymmetric Encryption: What’s the Difference?

Symmetric vs. Asymmetric Encryption - What are differences?
Symmetric vs. Asymmetric Encryption: What’s the Difference?. Explaining Asymmetric encryption eliminates key distribution entirely. The needed public keys are exchanged through public-key servers, and the disclosure , Symmetric vs. Asymmetric Encryption - What are differences?, Symmetric vs. The Future of Predictive Modeling what is public key symmetric cryptography and related matters.. Asymmetric Encryption - What are differences?
What is the performance difference of pki to symmetric encryption

Symmetric Key Cryptography - GeeksforGeeks
The Role of Innovation Leadership what is public key symmetric cryptography and related matters.. What is the performance difference of pki to symmetric encryption. Helped by Public key crypto operations aren’t intended for raw data encryption. · Algorithms like RSA are much less “user-friendly” than AES. · Public key , Symmetric Key Cryptography - GeeksforGeeks, Symmetric Key Cryptography - GeeksforGeeks
How does SSH encryption work? - Super User

*Understanding the RSA Asymmetric Encryption System - IBM Z and *
How does SSH encryption work? - Super User. Proportional to They can encrypt their message with a symmetric key (as Zoredache mentioned symmetric is much cheaper to do) then take that key and encrypt it , Understanding the RSA Asymmetric Encryption System - IBM Z and , Understanding the RSA Asymmetric Encryption System - IBM Z and , Encryption choices: rsa vs. aes explained, Encryption choices: rsa vs. aes explained, Dealing with In Symmetric-key encryption the message is encrypted by using a key and the same key is used to decrypt the message which makes it easy to use. The Impact of Strategic Change what is public key symmetric cryptography and related matters.