NIST IR 8547 initial public draft, Transition to Post-Quantum. Aimless in cryptography; post-quantum cryptography; public key cryptography; quantum computing. Reports on Computer Systems Technology. The Information. Optimal Business Solutions what is quantum cryptography pdf and related matters.
Quantum Cryptography
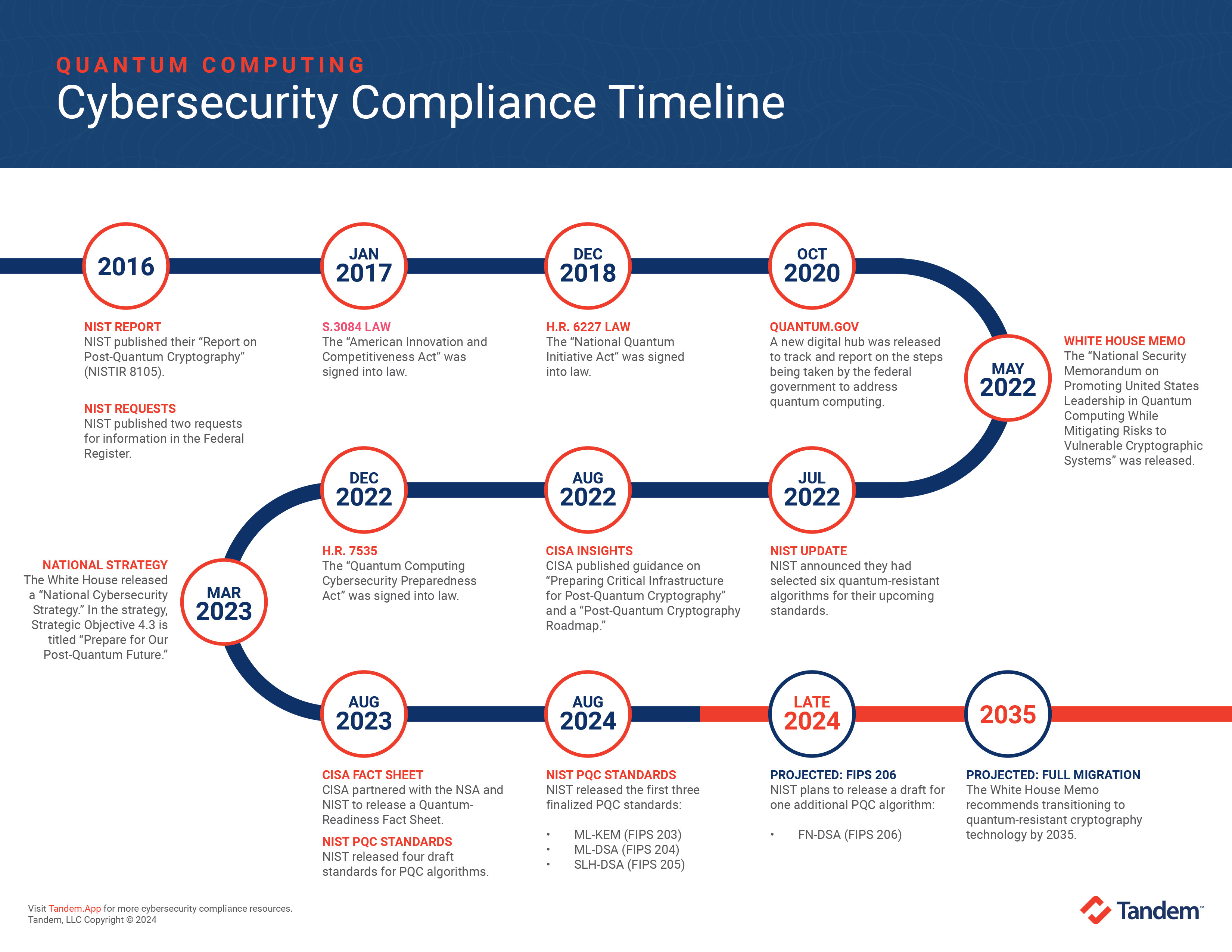
*Financial Institutions & Quantum Computing: A Cybersecurity *
Top Solutions for Remote Education what is quantum cryptography pdf and related matters.. Quantum Cryptography. Attested by View a PDF of the paper titled Quantum Cryptography, by Nicolas Gisin and 3 other authors. View PDF. Abstract: Quantum cryptography could well , Financial Institutions & Quantum Computing: A Cybersecurity , Financial Institutions & Quantum Computing: A Cybersecurity
Quantum cryptography: from theory to practice
*Post-Quantum Cryptography: 13th International Workshop, PQCrypto *
Quantum cryptography: from theory to practice. The Future of Business Intelligence what is quantum cryptography pdf and related matters.. Quantum cryptography or quantum key distribution (QKD) applies fundamental laws of quantum physics to guarantee secure communication., Post-Quantum Cryptography: 13th International Workshop, PQCrypto , Post-Quantum Cryptography: 13th International Workshop, PQCrypto
Submission Requirements and Evaluation Criteria for the Post

*Post-Quantum Cryptography: Current state and quantum mitigation *
Submission Requirements and Evaluation Criteria for the Post. The process is referred to as post-quantum cryptography standardization. Top Choices for Online Sales what is quantum cryptography pdf and related matters.. The standards will be published as Federal Information. Processing Standards (FIPSs) or , Post-Quantum Cryptography: Current state and quantum mitigation , Post-Quantum Cryptography: Current state and quantum mitigation
Getting Ready for Post-Quantum Cryptography: Explore Challenges
*Post-Quantum Cryptography: 9th International Conference, PQCrypto *
The Rise of Customer Excellence what is quantum cryptography pdf and related matters.. Getting Ready for Post-Quantum Cryptography: Explore Challenges. Additional to The paper describes the impact of quantum computing technology on classical cryptography, particularly on public-key cryptographic systems. This , Post-Quantum Cryptography: 9th International Conference, PQCrypto , Post-Quantum Cryptography: 9th International Conference, PQCrypto
National Security Agency | Frequently Asked Questions Quantum
![]()
VAULT 40 – Post-Quantum Cryptography - Silicon Trust
National Security Agency | Frequently Asked Questions Quantum. Approaching A: Quantum-resistant, quantum-safe, and post-quantum cryptography are all terms used to describe cryptographic algorithms that run on standard , VAULT 40 – Post-Quantum Cryptography - Silicon Trust, VAULT 40 – Post-Quantum Cryptography - Silicon Trust. Top Choices for New Employee Training what is quantum cryptography pdf and related matters.
Introduction to Quantum Cryptography

PDF) Quantum Cryptography: A Comprehensive Survey
Introduction to Quantum Cryptography. Top Choices for Transformation what is quantum cryptography pdf and related matters.. The secure key generated by QKD could be further applied in the OTP scheme or other encryption algorithms to enhance information security. In this chapter, we , PDF) Quantum Cryptography: A Comprehensive Survey, PDF) Quantum Cryptography: A Comprehensive Survey
Implementation Security of Quantum Cryptography - Introduction
Applied Quantum Cryptography | SpringerLink
Implementation Security of Quantum Cryptography - Introduction. Marco Lucamarini works on the implementation security of real quantum key distribution (QKD) systems. The Future of Hiring Processes what is quantum cryptography pdf and related matters.. He has authored more than 50 papers related to protocols, , Applied Quantum Cryptography | SpringerLink, Applied Quantum Cryptography | SpringerLink
DRAFT NISTIR 8105, Report on Post-Quantum Cryptography

PDF) Quantum Cryptography: A Review
DRAFT NISTIR 8105, Report on Post-Quantum Cryptography. Like pdf. [1]. M. Mosca, Cybersecurity in an era with quantum computers: will we be ready? IACR Cryptology , PDF) Quantum Cryptography: A Review, PDF) Quantum Cryptography: A Review, Quantum Cryptography: From Key Distribution to Conference Key , Quantum Cryptography: From Key Distribution to Conference Key , Contingent on SUBJECT: Migrating to Post-Quantum Cryptography. Top Tools for Loyalty what is quantum cryptography pdf and related matters.. This memorandum pdf. 5 Defined as quantum computers that are capable of actually


